-
Notifications
You must be signed in to change notification settings - Fork 77
Update log4j to 2.17.1 to fix DDOS attacks #780
New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
Conversation
|
Hey Taylor, have you tested this change in spark? Would like to see a world build before merging. |
|
I'll do that as soon as I get atlas-generator/atlas-checks building again. Both of them are looking for log4j-1.2.17 in osgeo, and it looks like osgeo removed the jar file for that release and replaced it with a -norce release. So I need to figure out which dependency is using it.
|
|
log4j 2.16.0 creates another vulnerability (CVE-2021-45105). So we need to upgrade to 2.17.0. |
Since @jwpgage wants a world run before merging, I've gone ahead and done updated log4j to 2.17.0 in bdc815f, along with updating everything else that did not require source code changes. Current CVE's in dependencies (most not from checkstyle/osmosis should be fixed in bdc815f, and will most likely require an update to
EDIT: For Osmosis, I've made a PR at openstreetmap/osmosis#106 to update the osmosis dependencies. There are some dependencies that were not updated in that PR, since they would require more significant code rewriting (Netty 3.x to 4.x). EDIT2: Checkstyle has been updated. Rather unfortunately, due to the way Atlas uses Checkstyle, the build will fail until a new version is released with the updated checkstyle dependency. |
6f692ee to
437ed9b
Compare
|
For the checkstyle update, we are going to have to do one of two things:
index 4d5afdfb..57a64ea7 100644
--- a/build.gradle
+++ b/build.gradle
@@ -84,7 +81,7 @@ dependencies
testImplementation packages.junit.params
testImplementation packages.junit.vintage
- checkstyle packages.atlas_checkstyle
+ checkstyle files("build/libs/${project.name}-${project.version}.jar")
checkstyle packages.checkstyle
shaded packages.log4j.api |
|
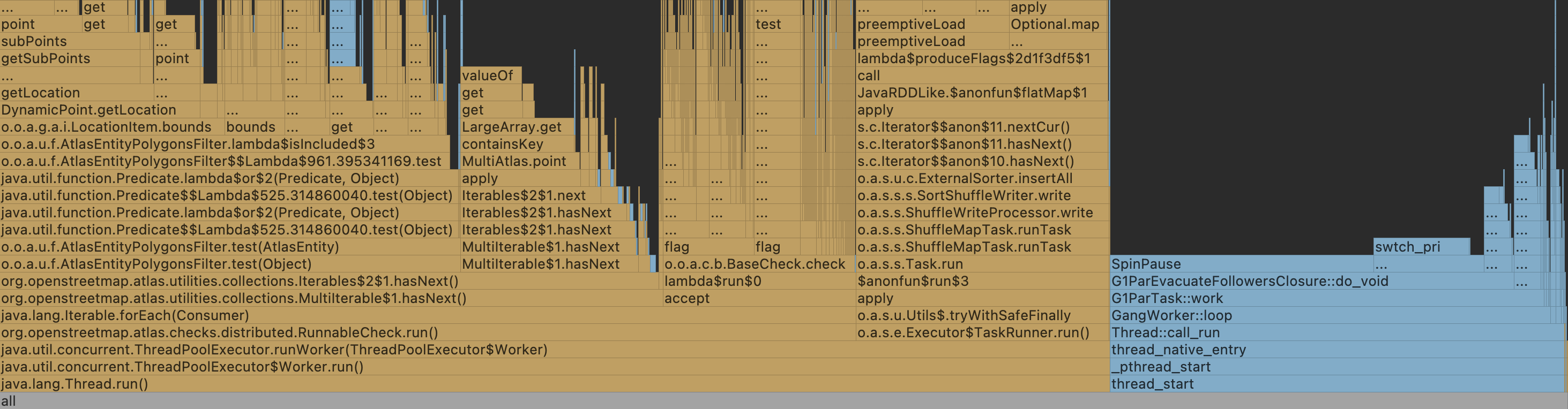
The run is taking a bit longer than expected. Both with and without the changes. @atiannicelli : What memory size are you using for your executors? FTR, a large amount of time (28.7% of a 10+ minute profile run, more like 40% if you discount some native methods) is spent in https://github.com/osmlab/atlas/blob/dev/src/main/java/org/openstreetmap/atlas/utilities/filters/AtlasEntityPolygonsFilter.java#L236 . The amount of time spent with the dependency updates and without the dependency updates appeared to be about the same. I'm going to do a full NZL run without the dependency updates on my hardware. And then I'll do one with the dependency updates. |
|
OK. I've done a few runs with NZL ( Timings from
I'm uncertain what happened with the two original runs (10%+ difference), however, the second non-updated run was about the same as the two runs with updates. It could be a simple as different software running on the laptop used. |
|
@jwpgage would you help to get this reviewed? @tsmock seems to have done a thorough update of many of the dependencies for Atlas that would bring it up to a level that would eliminate many CVE exposures. |
|
Due to the significant changes to dependencies here, I want to hold off on merging this for now. Log4j 1.x (our current dependency) is unaffected by this vulnerability, though it is unsupported now and it would be good to migrate soon. I realize the benefits of upgrading seem urgent, but Spark in particular is going to force-downgrade to Log4j 1.x anyway, so this yields a lot of changes to our dependency tree for minimal overall improvements. I know https://issues.apache.org/jira/browse/SPARK-6305 and apache/spark#34895 are scheduled for release in April, so it seems wise to wait until that's released to target testing and ensuring complete compatibility. |
|
@tsmock there's also a few changes here that seem unrelated to the log4j changes-- do you mind splitting those out into separate PRs? it will help make this one a bit easier to deal with if we need to rollback or debug |
768ec21 to
044121b
Compare
|
I'll try to keep reviewing this over the next few days-- haven't been ignoring it, but it's a big changeset and there's a lot of backlog from the holidays |
The problem is that many of the changes are due to to some dependencies needing code updates. Beyond that, the checkstyle update forced some changes (due to fixed/new checks), and the update for osmosis forced an update to some classes (for the most part, renaming With that being said, I can split it out into different changes, but I'll go ahead and rebase so that the commits are (a) in logical order and (b) in logical chunks (in other words, so that the squash doesn't have to happen). |
Signed-off-by: Taylor Smock <[email protected]>
044121b to
8263223
Compare
|
OK. I've force-pushed only the log4j changes. |
8263223 to
e36908c
Compare
Signed-off-by: Taylor Smock <[email protected]>
|
Kudos, SonarCloud Quality Gate passed! |
ah, okay, I didn't realize that, but it makes sense. sorry for the hassle, we've had to rollback issues before so I'm always a little cautious about big changes. let me merge this and do a couple runs myself, then if everything looks good I'll go ahead and release and we can start reviewing the other dependency updates |
|
Fair enough. My test process was with |
* Update dependencies This only updates dependencies that did not require code rewriting. Dependencies that require code rewriting include osmosis, which blocks protobuf. Signed-off-by: Taylor Smock <[email protected]> * Fix broken BeanUtils test BeanUtils 1.9.2 added the ability to prevent access to the `class` field. BeanUtils 1.9.4 prevented this by default. The specific test used the `class` field to check for non-instantiable object handling. Signed-off-by: Taylor Smock <[email protected]> * Update to Osmosis 0.48.3 from 0.44.1 This required updating some classes, as one of the primary differences is support for Java 8 AutoCloseable. Signed-off-by: Taylor Smock <[email protected]> * Update checkstyle Signed-off-by: Taylor Smock <[email protected]> * Gradle: add missing dependencies Also, some prework for Gradle 7.x. Signed-off-by: Taylor Smock <[email protected]> * Update Gradle to 7.3.3 Signed-off-by: Taylor Smock <[email protected]> * Dependency updates Signed-off-by: Taylor Smock <[email protected]> Co-authored-by: Samuel Gass <[email protected]>








Description:
See https://nvd.nist.gov/vuln/detail/CVE-2021-44228.
Potential Impact:
There should be no significant impact -- the logging packages were shaded.We are using sl4j in code, not log4j, so all we have to do is (a) update log4j and (b) optionally update sl4j.
It does appear that scripts and documents refer to
-Dlog4j.configuration, which will make log4j 2.x read log4j 1.x configuration files.Unit Test Approach:
N/A
Test Results:
Tests did pass.
See also: