-
Notifications
You must be signed in to change notification settings - Fork 220
Bug 1962502: Add alerts for unmanaged Routes and Ingresses without IngressClassName #823
New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
Bug 1962502: Add alerts for unmanaged Routes and Ingresses without IngressClassName #823
Conversation
|
Skipping CI for Draft Pull Request. |
|
@suleymanakbas91: This pull request references Bugzilla bug 1962502, which is valid. The bug has been updated to refer to the pull request using the external bug tracker. 3 validation(s) were run on this bug
Requesting review from QA contact: DetailsIn response to this:
Instructions for interacting with me using PR comments are available here. If you have questions or suggestions related to my behavior, please file an issue against the kubernetes/test-infra repository. |
9916d88 to
1898399
Compare
|
@suleymanakbas91: This pull request references Bugzilla bug 1962502, which is valid. 3 validation(s) were run on this bug
Requesting review from QA contact: DetailsIn response to this:
Instructions for interacting with me using PR comments are available here. If you have questions or suggestions related to my behavior, please file an issue against the kubernetes/test-infra repository. |
|
/retest |
|
/assign |
|
/retest |
1898399 to
959b73b
Compare
|
/retest |
1 similar comment
|
/retest |
|
/label qe-approved Verified via pre-merge workflow. For more details : https://bugzilla.redhat.com/show_bug.cgi?id=1962502#c7 |
|
/retest |
3 similar comments
|
/retest |
|
/retest |
|
/retest |
|
@suleymanakbas91: This pull request references Bugzilla bug 1962502, which is valid. 3 validation(s) were run on this bug
Requesting review from QA contact: DetailsIn response to this:
Instructions for interacting with me using PR comments are available here. If you have questions or suggestions related to my behavior, please file an issue against the kubernetes/test-infra repository. |
|
/retest-required |
|
Strange test result. It doesn't like the Alerts, but I don't think this has anything to do with the new Alerts.
/test e2e-aws-ovn-upgrade |
@candita The following image shows |
|
Failures seem to be unrelated.. /retest |
|
Unrelated failures.. /retest |
|
/approve |
|
/test e2e-aws-operator |
|
[APPROVALNOTIFIER] This PR is APPROVED This pull-request has been approved by: candita The full list of commands accepted by this bot can be found here. The pull request process is described here DetailsNeeds approval from an approver in each of these files:
Approvers can indicate their approval by writing |
|
/lgtm |
|
/test e2e-aws-operator |
|
/retest |
5 similar comments
|
/retest |
|
/retest |
|
/retest |
|
/retest |
|
/retest |
|
/test e2e-aws-operator |
|
/retest |
2 similar comments
|
/retest |
|
/retest |
|
e2e-aws-operator failed because kube-apiserver reported |
|
@Miciah: Overrode contexts on behalf of Miciah: ci/prow/e2e-aws-operator DetailsIn response to this:
Instructions for interacting with me using PR comments are available here. If you have questions or suggestions related to my behavior, please file an issue against the kubernetes/test-infra repository. |
|
@suleymanakbas91: all tests passed! Full PR test history. Your PR dashboard. DetailsInstructions for interacting with me using PR comments are available here. If you have questions or suggestions related to my behavior, please file an issue against the kubernetes/test-infra repository. I understand the commands that are listed here. |
|
@suleymanakbas91: All pull requests linked via external trackers have merged: Bugzilla bug 1962502 has been moved to the MODIFIED state. DetailsIn response to this:
Instructions for interacting with me using PR comments are available here. If you have questions or suggestions related to my behavior, please file an issue against the kubernetes/test-infra repository. |
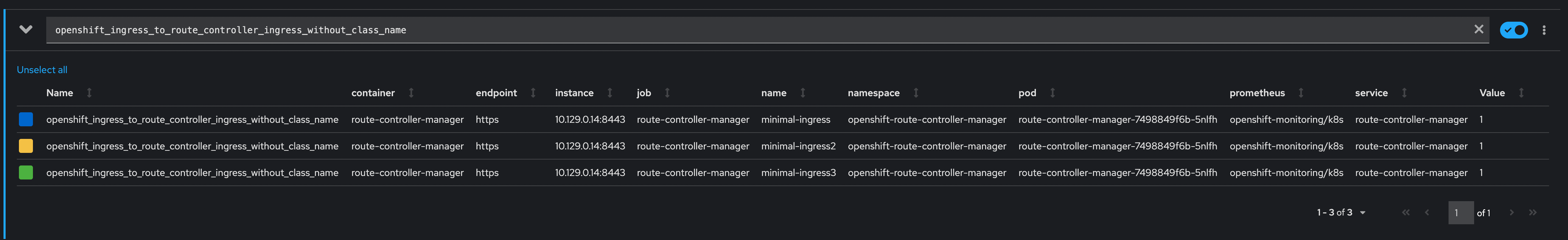
This PR adds two new alerting rules
IngressWithoutClassNameandUnmanagedRoutesthat use the custom metrics created inopenshift/route-controller-manager#8.
IngressWithoutClassNamefires when there is an Ingress with an unset IngressClassName for longer than one day.UnmanagedRoutesfires when there is a Route owned by an Ingress no longer managed.