Merged
Conversation
It's not working when constructing it in-place, likely this is undefined behaviour. Co-authored-by: Paul Kramer <paul.kramer@logmein.com>
This should result in a address of temporary array. Co-authored-by: Paul Kramer <paul.kramer@logmein.com>
There are two different API's in OpenSSL for configuring TLS ciphers, one for TLS 1.2 and below, and another for TLS 1.3. coturn only calls the TLS 1.2 API when handling the `--cipher-list` configuration option, which means that it's not possible to use non-default ciphersuites with TLS 1.3 connections. This PR calls appropriate OpenSSL API to allow TLS 1.3 ciphersuites to be configured.
Somewhat relevant to #1075
Since winsock do not use errno, and have different error codes, this is needed to be windows compatible This pull request is a split of PR #1061
This is not a long term documentation works - this is a temp proposal to modernize existing documentation - Create docs folder - Move existing documentation files into docs - Split one massive INSTALL files into smaller files (no text editing was done except small markdown header formatting) - Rename files to be markdowns for nicer rendering - Bad md rendering is expected in many places
Add some basic contributing guidelines based (almost cloned) on the Redis ones. There were some questions about how to contribute and get started with the project. I see this type of document in other projects that I think can be useful.
This pull request is a split of PR #1061 As @KangLin pointed out in the original PR those sockets should ideally be permanently non-blocking for performance reasons, but they are NOT at the moment. Someone with more knowledge about the code in dtls_listener.c should probably have a look if it would be feasible to change the sockets to non-blocking already at creation, similar to what is done in udpserver.c...
MacOS CI build started to fail in the PRs because when upgrading python it was not possible to override one existing file (related to 2to3 package). Apparently this happens because MacOS runners some times have python versions not installed/compatible with brew. Example of the failure: https://github.com/coturn/coturn/actions/runs/3850951324 The proposed workaround is taken from here: actions/runner-images#2322
Noticed the plaintext password of my postgresql server in my coturn logs, but postgresql errors would return the password sanitised. Simple fix to log the sanitised string. 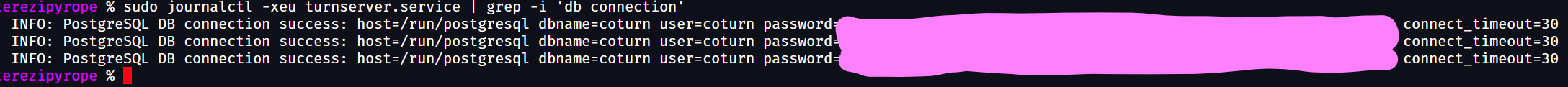 Signed-off-by: r3g_5z <june@girlboss.ceo> Signed-off-by: r3g_5z <june@girlboss.ceo>
There is no reason to include the license of openssl - coturn uses openssl just like any other library As a reference - Apache httpd does not have openssl license #1049
Co-authored-by: Kai Ren <tyranron@gmail.com>
…pshot to fix CVE-2023-0286 (and friends) in Docker image
In some cases the prometheus server was started using SELECT even if EPOLL was supported. Some flags were changed in microhttpd and now we use MHD_VERSION to make sure to use the right ones in all cases (support old version, for ubuntu 16.04 for ex). This fixes the issue #1167 I also added a log to make sure we know which version is used, especially to inform the user that the SELECT version might lead to issues on highly used servers.
…pshot to fix CVE-2023-0464 and CVE-2023-0465 in Docker image
Removing windows.h inclusion, not needed with ws2tcpip.h. Causes some struct redefinitions.
Update version number, generate authors and changelog files Release notes (short summary of changes) ``` - Make sure microhttpd starts using epoll if supported - Add sessioncount to prometheus metrics - Add STUN request/response/error prometheus counters - Cleanup logs on turnserver start - Fix duplicate stdout log output - Log threadId to logs to aid in multi-threaded debugging - Optional build info compiled into turnserver binary - Fix arguments expansion in `docker-entrypoint.sh` - Santise database connection strings before printing to log - Support Windows MSVC - Add configuration option for TLS 1.3 ciphersuites - Improve openssl3 and FIPS support - Use single SSL_CTX for TLS and DTLS support - Update openssl API use to non-deprecated version - Set string bytes to null to prevent random origin - Fix memory corruption on socket close - Fix packet backlog fifo that processed packets in reverse order in some scenarios - Fix off-by-one when terminating gcm_nonce - Fixes to Redis memleaks and socketleaks - Fix malformed response to mobility refresh request - Fuzzing support - Ignore raw UDP if no_udp is enabled - Better detect availability of SCTP protocol ``` --------- Co-authored-by: tyranron <tyranron@gmail.com>
Additionally: - update Debian "bullseye" to 20230411 snapshot in Docker image
Co-authored-by: Kai Ren <tyranron@gmail.com>
This file contains hidden or bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
Sign up for free
to join this conversation on GitHub.
Already have an account?
Sign in to comment
Add this suggestion to a batch that can be applied as a single commit.This suggestion is invalid because no changes were made to the code.Suggestions cannot be applied while the pull request is closed.Suggestions cannot be applied while viewing a subset of changes.Only one suggestion per line can be applied in a batch.Add this suggestion to a batch that can be applied as a single commit.Applying suggestions on deleted lines is not supported.You must change the existing code in this line in order to create a valid suggestion.Outdated suggestions cannot be applied.This suggestion has been applied or marked resolved.Suggestions cannot be applied from pending reviews.Suggestions cannot be applied on multi-line comments.Suggestions cannot be applied while the pull request is queued to merge.Suggestion cannot be applied right now. Please check back later.
PR Submission Checklist for internal contributors
The PR Title
SQPIT-764The PR Description
What's new in this PR?
Issues
Briefly describe the issue you have solved or implemented with this pull request. If the PR contains multiple issues, use a bullet list.
Causes (Optional)
Briefly describe the causes behind the issues. This could be helpful to understand the adopted solutions behind some nasty bugs or complex issues.
Solutions
Briefly describe the solutions you have implemented for the issues explained above.
Dependencies (Optional)
If there are some other pull requests related to this one (e.g. new releases of frameworks), specify them here.
Needs releases with:
Testing
Test Coverage (Optional)
How to Test
Briefly describe how this change was tested and if applicable the exact steps taken to verify that it works as expected.
Notes (Optional)
Specify here any other facts that you think are important for this issue.
Attachments (Optional)
Attachments like images, videos, etc. (drag and drop in the text box)
PR Post Submission Checklist for internal contributors (Optional)
PR Post Merge Checklist for internal contributors
References
feat(conversation-list): Sort conversations by most emojis in the title #SQPIT-764.