-
Notifications
You must be signed in to change notification settings - Fork 33
Encryption
megli2 edited this page Jul 19, 2023
·
11 revisions

| Name | Description |
|---|---|
| private_key encrypted | Private RSA key encrypted with user's password |
| private_key | Unencrypted private RSA key to decrypt team passwords |
| public_key | Public RSA key to encrypt team passwords |
| Clear-text team-password | Password from team as clear-text. Password is a randomly generated AES-256 key |
| Encrypted team-password | Team-password encrypted with public RSA key |
| Random transfer-password | Random password generated to encrypt an encryptable which is going to be transferred |
| Encrypted random transfer-password encrypted | Random transfer-password encrypted with receivers public_key |
| Clear-text encryptable data | encryptable data(password, username, attachment, token, pin, email, custom attribute) as clear-text |
| Clear-text encryptable data | encryptable data(password, username, attachment, token, pin, email, custom attribute) encrypted with public with teampassword |
| Clear-text user-password | Password from user as clear-text |
| Encrypted user-password | User-password encrypted with public RSA key |
| User Bob | An example user named Bob |
| User Alice | An example user named Alice |
| What | Keylength |
|---|---|
| RSA Keys | RSA 2048 |
| Team Password | AES 256 |
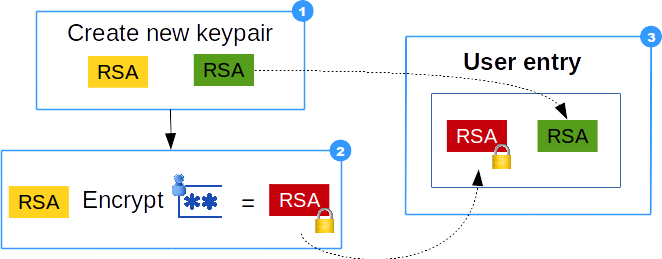
- A new RSA key pair is generated
- RSA private key is encrypted with user's password
- RSA key pair saved as User attributes
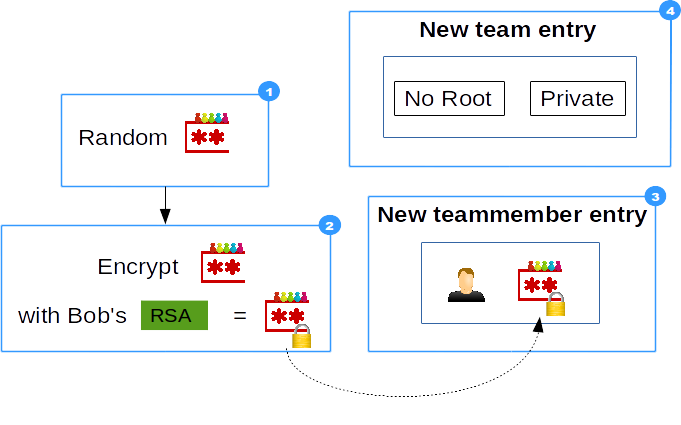
- Random AES-256 key is generated as team-password
- Team-password is encrypted with Bob's public key
- Encrypted password saved as Teammember attribute
- if private: admins will not have access on this Team
There will be no passwords in the model Team
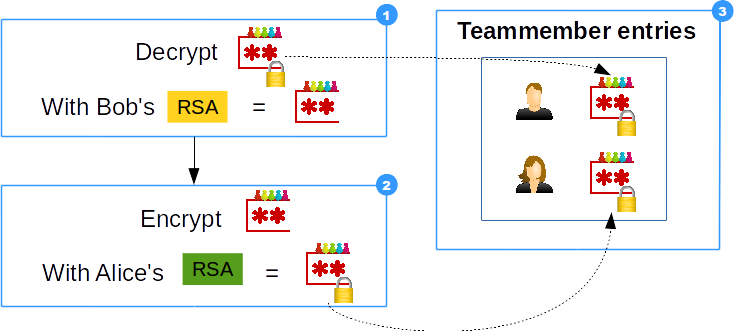
- Encrypted password is decrypted with Bob's private key
- Team-password is encrypted with Alice's public key
- Encrypted password saved in new Teammember as attribute
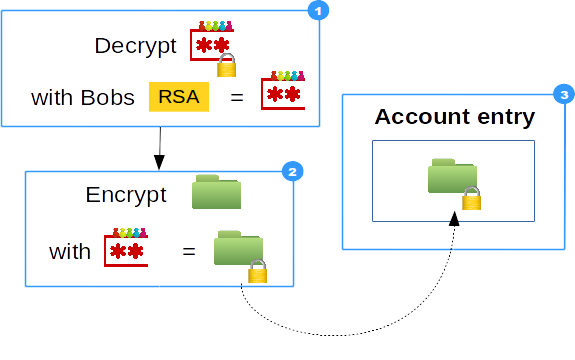
- Encrypted team-password is decrypted with Bob's private key
- Encryptable-data is encrypted with plain-text team-password
- Encrypted encryptable-data saved as Encryptable attributes
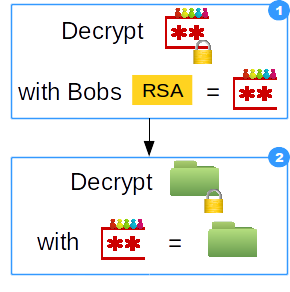
- Encrypted team-password is decrypted with Bob's private key
- Encrypted encryptable-data is decrypted with plain-text team-password
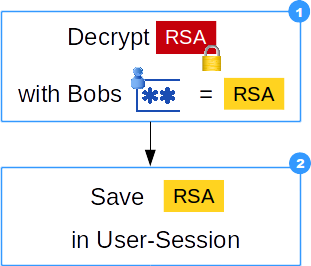
- Decrypt encrypted private RSA key with Bob's plain-text user-password
- Save decrypted private RSA key in Session
The private RSA key will never be saved in plain-text except in a session!
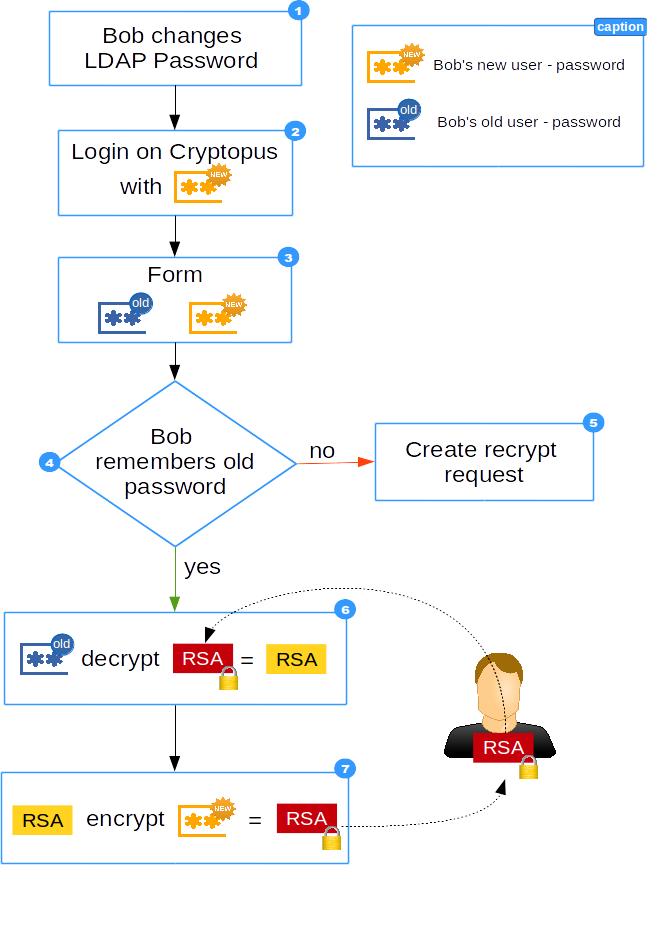
- The user Bob changes his LDAP passowrd
- Bob login on Cryptopus with his new password
- A Form will be shown, in which Bob must enter the new and the old password
- Does Bob remember the old password?
- If not a new recrypt request will be created
- Else, decrypt encrypted private key with old password
- Encrypt private key with new password and save in DB
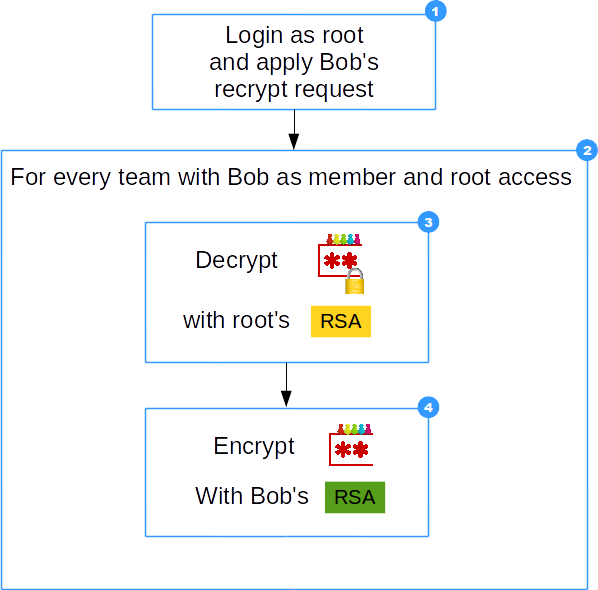
- Root logs in and applies Bob's recrypt request
- Process all teams with Bob's membership which are accessible by root
- Decrypt encrypted team-password with root's private key
- Team-password is encrypted with Bob's new public key
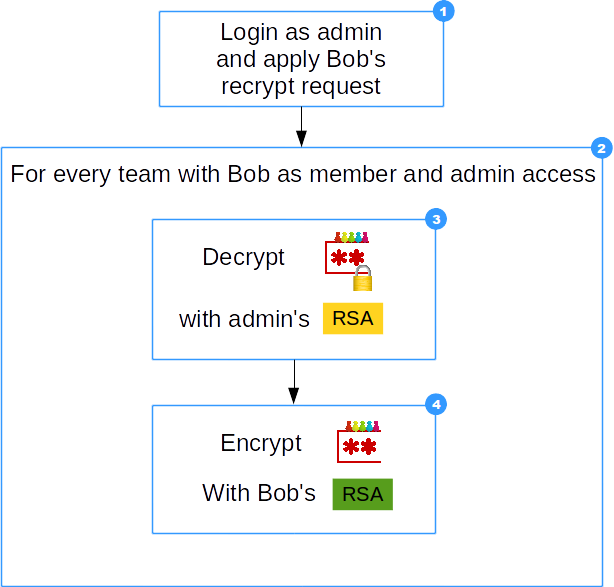
- Admin logs in and applies Bob's recrypt request
- Process all teams with Bob's membership which are accessible by admin
- Decrypt encrypted team-password with admin's private key
- Team-password is encrypted with Bob's new public key
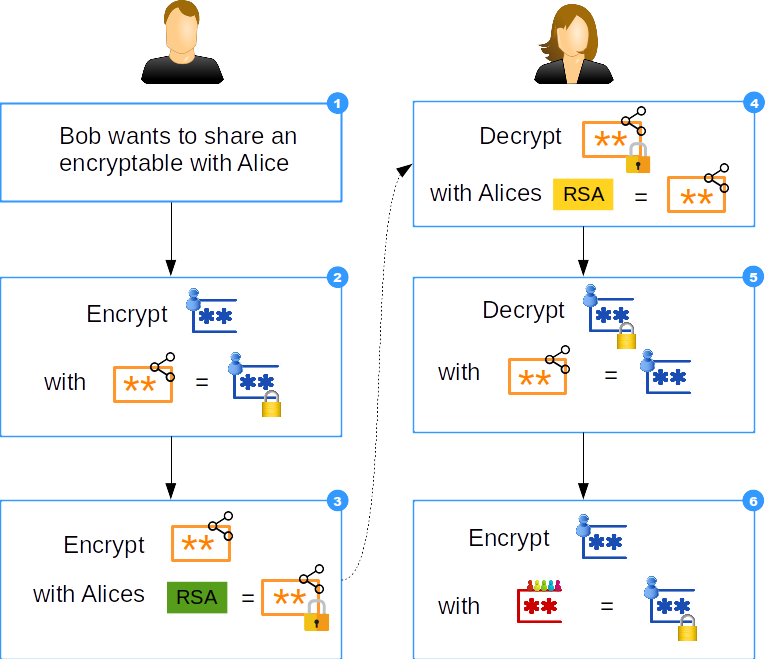
- Bob wants to share an encryptable with Alice
- He encrypts the encryptable with a random transfer password
- Then He encrypts the random transfer password with the public key of Alice
- Afterward Alice decrypts the random transfer password with her private key
- With the random transfer password she is now able to decrypt the encryptable
- The cleartext encryptable is then finally encrypted with the personal team password of Alice