-
Notifications
You must be signed in to change notification settings - Fork 25
New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
No stats after firmware update #86
Comments
|
To me it looks like the Onewheel now requires some kind of initialistaion to send values. |
|
Just noticed the same thing with Onewheel Community Edition app. I only get firmware and hardware revision. Almost all properties in LightBlue are also unnamed now. Going to investigate today with a phantom board and will let you know if I find anything useful. |
|
Hmm well that's a bit annoying. If not solved I'll tackle in a few days, my XR is out as I change to a new treaded tire (currently stuck at the dismount step, it isn't easy as YouTube peeps show). I doubt the GUIDS changed but hard to say ... Likely will just reverse the official app. |
|
GUIDs are the same. Only firmware and hardware revisions have values via LightBlue. The latest official app doesn’t detect my phantom board for doing the reverse engineering of their BLE anymore. Previous app versions still work fine. Another thing is the URL path for the new firmware has changed. And a few other things about the apps are different. I wonder if all of this is FM trying to prevent these 3rd party apps existing? EDIT: I updated my Android device to the latest OW app. I enabled HCI logging and then connected to the board and then sent the log to my computer and am stepping through it with Wireshark. I can see the app fetching ride mode fine and on the correct characteristic uuid. I am looking up back further to see if the board is sending any specific data to allow it to send the other data. Will update when I know more. |
|
Using gatttool its reading 0 for alot of handles, some have data but how is one to map them to meaningful names? |
|
Inspecting a bluetooth log, I am 99% confident the uuids have not changed and don’t need to be renamed. The board is doing something else. Should also be noted the old OW app can’t connect to the new OW board, much like the same issue we are in. |
|
Yes I can confirm this. The characteristics are still the same. |
Do you mind uploading your HCI log? |
|
e659f31d through to e659f320 are not new. LightBlue used to have named properties and it would call them unknown 1 to unknown 4. I don't believe I've ever seen them change value, but they could very we be used now though. Log is attached, it can be opened by Wireshark. It also shows my device picking up a bunch of other devices so need to double check for service UUID and then compare it. From memory board connects in frame 117. EDIT: There is also bluetooth logging for iOS. I didn't know it was a thing otherwise I probably would have tried this. https://developer.apple.com/bug-reporting/profiles-and-logs/ |
|
Ok thanks, maybe I can spot something new. |
|
So that's what I've discovered:
The interresting one is the serial data. I couldn't make sence of it, but it's probably just in a wrong endian right now. |
|
Could you please provide a few more log files with connection establishments so I can validate my theory? |
|
The serial write one is interesting. I've only seen the board do serial write for firmware deploying. I'd be interested to know:
For other people to get the data its really easy on Android if you have dev mode unlocked. http://www.fte.com/WebHelp/BPA600/Content/Documentation/WhitePapers/BPA600/Encryption/GettingAndroidLinkKey/RetrievingHCIlog.htm Ill go check on Facebook if I can get anyone else to generate a log. EDIT: In case anyone comes across this thread, that above link shows how to enable HCI logging. Here is an app that can open that log file and allow you to share it. |
|
Here is another log. Here is what I have found so far. This could just be an order of operations in a multi threaded app, or it could be how it triggers the board to send some sort of data as a key. But on frame 342 it enabled read notifications on E659F3EE which is interesting because that IS a new characteristic which isn't exposed when we can the boards characteristics. Once notifications are enabled it writes the boards firmware revision back to itself. After that 20 bytes of data is received as notifications from the previous subscription (below as each notification)
After that 20 bytes of data is sent back to the board on E659F3FE (which as you said was serial read previously (its odd that the first 3 bytes match, they would be the characters CRX if that means anything to anyone? Some of the other bytes are in the string, others are not found. Also note it is ).
Also note it is slightly different from the value in my last log. Its the same length and starts with the same 3 bytes.
And for reference, from scan 1, here is the 20 bytes that where sent from the board to the phone.
After that the E659F3EE characteristic which I believe is the new serial read starts spitting out the gibberish it used to. I reckognise it because it'd keep saying "One" and some data between it. I never did figure out what it all meant. At frame 382 the notification for E659F3EE is disabled and then it seems that the board communicates as usual with its reads and writes how our apps used to. After work tomorrow I am going to double check these values along with the endianness and see what they could possibly be. |
|
I will try to reverse engineer the .apk. Maybe I can spot something there. |
|
I had tried that a few days ago, but It appears to be obfuscated very differently to how it used to be. Either that or my new dev setup isn't working right. |
|
Yeah, it's been minified :( Makes it very hard to read. |
|
All this makes me think they really don't want 3rd party apps. Surely this wasn't all on accident :P |
|
A little bit more "security" is not wrong. They had some really big flaws, because everybody was able to connect to your oneweel and for example change light mode or change riding mode during the ride. |
|
*had and still have |
|
You're right, extra security is never a bad thing. If only there was a bug bounty program or similar to receive free XRs. |
|
Awesome everyone here is tackling this... I just did an initial look at the APK (using jadx for decompilation) and looks like they are doing some encoding/decoding with the chars on the top layer. I take it the messages are still coming through, just garbage until we figure out the seed and key values. They also moved a lot of the methods handling sensitive and private data to native, just making it slightly more annoying to reverse, including MainActivity.getChallengeResponsePassword below. com.rideonewheel.onewheel.OnewheelService |
|
Going to continue tomorrow, here's what I've found out so far: public void a(byte[] paramArrayOfByte)
{
if (this.D != null) {
a(this.D, paramArrayOfByte);
}
}
private e.a af = new e.a()
{
public void a()
{
OnewheelService.b(OnewheelService.this);
}
public void a(byte[] paramAnonymousArrayOfByte)
{
OnewheelService.this.a(paramAnonymousArrayOfByte);
}
}; |
|
E659F300-EA98-11E3-AC10-0800200C9A66 is the service UUID. I just got sent someone elses log and I got the same thing, read 20 bytes, did something and then sent those 20 bytes off. Could you find E659F3EE-EA98-11E3-AC10-0800200C9A66 anywhere? EDIT: @jj05y yeah I think writing of the board firmware version back is triggering the board to then send us the password for the device. And yeah reading it is for figuring out what flow we want to then follow makes sense. @kwatkins Can we able to see the contents of the getChallengeResponsePassword like your above code or does it not get decompiled? |
|
fyi, just trying to work out the flow of what the official app is doing, may/may not help the research going on now. let me know if there are places to zero on and i can continue the dive. |
|
@COM8 I was planning on doing that, but I can't find a good way outside of the customer support system. Any ideas? |
|
One way would be creating a thread in the forum. |
|
Last time I did that just mentioning my app existed they deleted my thread, there's no way they would leave that up. |
|
If they delete our post we know they wouldn't answer us via mail/support. I'm the dev of XYZ and I would like to know what's up (or so). The thread has to get some attention form normal people and staff |
|
Forum Moderators and policy makers at FM are probably not the same people, they may just not want drama in their forums. Does anyone know if the OWBuddy guys still work at FM and how to contact them? They seem like the perfect people to ask |
|
Next chapter as I try to solve the Play store version mystery using an old Galaxy S4 on Android 5.0.1. Factory reset + sign in with my own Google account = access to newest 3.4/Gemini version according to the Play store page. I verified that it could connect to my OW+ successfully. So bottom line is that using Android 5.0(.1) pOnewheel can be retrieved from the Play store IF the Google account have access to it... @kwatkins any idea why only some Google accounts can access version 3.4 of pOnewheel? |
|
If I had to guess, he used the staged rollout feature, whether he intended to or not, which just rolls out the update to a select % of users. It's used mostly by big apps who only want to have 5% of their users experience horrible undiscovered bugs instead of all 100% :p |
|
It's a partial rollout (33%) to get logs, make sure it's stable. And it
doesn't appear to be, lots of ANR's. More people testing here it the
better, especially developers, when I get a chance dive deeper into what is
causing the crashes and report back here.
…On Sat, Feb 2, 2019 at 9:03 AM Nanoux ***@***.***> wrote:
@COM8 <https://github.com/COM8> I was planning on doing that, but I can't
find a good way outside of the customer support system. Any ideas?
—
You are receiving this because you were mentioned.
Reply to this email directly, view it on GitHub
<#86 (comment)>,
or mute the thread
<https://github.com/notifications/unsubscribe-auth/AA0LrVe7LE5kHHVmqVqzEcjm8JPmnXQOks5vJcTEgaJpZM4YnXma>
.
|
|
@nanouX exactly.
Also, from reading the unfortunate DMCA news from this thread - the
genesis of this app was to collect data, a black box recorder of sorts to
help diagnose wtf was happening with all the nose dives... FM wasn't
helping the us figure it out with their heads in the sand. And the
information we get from the app also shows placement of foot sensors, when
they are engaged, again, this is all safety stuff beyond what the official
app or FM talks about.
Annoying to say the least.
…On Sat, Feb 2, 2019 at 3:38 PM Nanoux ***@***.***> wrote:
If I had to guess, he used the staged rollout feature, whether he intended
to or not, which just rolls out the update to a select % of users. It's
used mostly by big apps who only want to have 5% of their users experience
horrible undiscovered bugs instead of all 100% :p
—
You are receiving this because you were mentioned.
Reply to this email directly, view it on GitHub
<#86 (comment)>,
or mute the thread
<https://github.com/notifications/unsubscribe-auth/AA0LrQQ2e5-1zI7HtXT_GbuVN9Lgdapfks5vJiFmgaJpZM4YnXma>
.
|
|
Looking through it really quick, I might know why its happening. In your OnServicesDiscovered function, you setNotify & read every bluetooth characteristic you want, and then do the gemini thing as you get the value for the firmware version. In my experience, the values you setNotify initially will work, but anytime you try to setNotify or un-setNotify (not great with the lingo, sorry), or try to read a characteristic, you get null values. Heres the flow in my app: That will get you connected, but if you want to do it reliably theres a few tips I found. If you try to reconnect within 24 seconds of the last handshake, for some reason the onewheel sends more than 20 bytes. Like, a lot more. If you do the same hash thing with the first 20 bytes it sends it will still connect, but you have to do something like (inkey.toByteArray().length >= 20) in you gemini function, and put in some logic so that it only executes once and not every time you recieve a byte after the first 20. Also in this case, writing the characteristic usually fails. gatt.writeCharacteristic returns a boolean to tell you if it worked, and when you try to reconnect in this window it usually fails. I just wait a bit and then keep trying, over and over, until it works, but there may be a better solution. Also, I had a super weird bug on my Pie Pixel where if I tried to read the firmware version immediately in OnServicesDiscovered, the connection would sometimes instantly time out, so I used a Handler thread to delay it 500 ms and that makes it a lot more stable, so do with that what you will. Anyway, I hope this helps @kwatkins , if you have questions or want a flowchart or something lemme know :P EDIT: If i can find the time I'll try and add these myself, but between college, work, and trying to save my own app I don't know if that'll happen. But I'll try. |
|
@nanouX Thanks for this helpful insight! |
|
@nanouX +1 to the thanks, super helpful. I'll implement this workflow when cycles open up, have a newborn/little dude and dirty diapers to change before changing my dirty code ;) As always appreciate the help from everywhere here, and definitely open to others implementing this, I can help test and roll out the changes. |
|
I was thinking, does Bluetooth the company have any rules about restricting access to a Bluetooth device in order to get licensed? I can't find anything but that seems like it should be a thing. |
|
@nanouX About 10 years ago, I attended several so-called UPF events (UnPlugFest) organized by the Bluetooth SIG. The Bluetooth SIG itself is an association of different Bluetooth device/chip manufacturers that drive the development of new features of this manufacturer-independent forward. Back then, it was obligatory for every manufacturer of Bluetooth enabled devices to have their product/platform certified by the Bluetooth SIG. Each platform was certified for implementing a minimum set of Bluetooth functionality so that it is entitled to wear the Bluetooth brand... (Fee for this was about 10k$ per platform) FM uses a Bluetooth SoC that was developed by TexasInstruments. In this case - I believe - it is sufficient that the SoC module is certified. The Bluetooth SIG itself does not enforce rules that guarantee a safe/secure use of the Bluetooth wireless technology. Due to the high segmentation, it is almost impossiblke for them to monitor all use-cases of Bluetooth technology. Long answer short: I do not think so. |
|
Alright, thanks, that's quite helpful. I'll probably write a message to FM customer support sometime in the next few days and hope for the best, really not much else I can do it seems. |
|
Update: Customer Support ticket has been sent, I couldn't find any other way of contacting FM I open sourced the free version of Onewave and put a built, unsigned APK in a release for anyone desperate. This class may be of interest to you guys, Its diverged quite a bit from when I got it from the pOnewheel source but it should be quite useful nonetheless. https://github.com/Nanoux/Onewave/blob/master/app/src/main/java/com/nanowheel/nanoux/nanowheel/util/BluetoothUtilImpl.java EDIT: Just wanted to thank @kwatkins and anyone whos worked on this project, reverse engineering it taught me so much about Android Development and specifically how to connect to BLE. |
|
Has anybody tested the unlock mechanism with a OW+XR? |
|
Ok, yes confirmed: To unlock an OW+XR we need to listen for and write back the 4134 (0x1026) FW revision instead of the 4034 (0x0fc2) FW revision of an OW+. Thanks to @TomasHubelbauer. |
|
5686... That is a huge firmware jump, and odd that it isn't 5086 or something. I assume it's via analytics? Any idea of rough location, like California maybe? |
|
@beeradmoore My bad, that was a messup on my part! I was looking at a wrong buffer 🙄 |
|
Damn, got me excited for a new OW being discovered in the wild :p (I guess they wouldn't use 3rd party apps to test the new OWs for this very reason). @jj05y this can probably all be closed now. |
|
@nanouX Any news about your ticket? |
|
Anyone here planing to get the new Pint board? |
|
Yep to the Pint board, although others may get it before me as I wait for it to ship (and clear customs) to Australia. |
|
They closed my ticket without notifying me or even speaking to me ~ 2 weeks after I filed it. Honestly I dunno if I want it to exist in spite of FM or not. I want a pint so bad, it looks like it solves all the problems I have with my +, just can't afford it rn without selling my current board, which I need for school. Is ponewheel ok @kwatkins ? I havent gotten the gemini update on my phone and im in the beta channel. We may have a new connection method to crack when pints come out. I would also really like to know if custom shaping is just locked out in the app and 3rd party apps could enable it. That would be interesting and explain a lot. |
|
Closing this ticket since we got support rolled in... other tickets are/will be/have been spun out from this one for sure. |

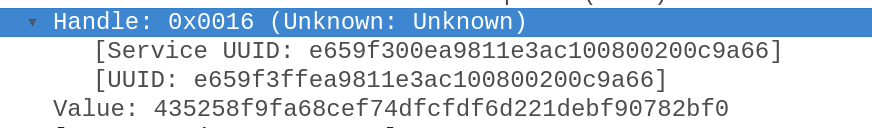
Hey,
I just cloned the repo and while the app connects fine, there's no stats available. It may be the firmware update. Can you repro?
The text was updated successfully, but these errors were encountered: