-
-
Notifications
You must be signed in to change notification settings - Fork 1.5k
New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
Make {PICKCHARS} possible [$50] #725
Comments
|
I still think this is an antipattern fad that is going to go away. Cool dialog though |
|
Antipattern or not - it is still a valuable feature for logins in various locations that still require selective character input. For me it's the only thing that forces me to use a regular KeePass from time to time. It would be great if I could use KeePassXC for every use case I have. 👍 to that. |
|
To be honest, I didn't even know this broken authentication scheme was even a thing until people started bringing it up. |
|
I think this will remain in wishlist for a long time |
|
I think #820 has been referenced in error, these are two distinct suggestions/features. |
|
It was a specific comment that I was referencing. Here Santander is using a bad practice authentication. I'm really not interested in developing a tool that will increase the adoption of such a system. |
|
Again, denying this option to KPXC users will NOT make Santander (or any other banking system - seems that only those use it) forfeit this login method. Some people are stuck with certain banking solution and as long they have no other option, KPXC is useless. Imagine using a business account, where you have no saying in which bank is contracted. What would you rather see? A user not relying on kdbx and using memorized/written down, fairly simple password or a user that is doing everything he can in order to make everything as secure as possible on his side? Do what ever you think is right, but from my point of view you're declining the feature while blaming the wrong side. And no, those passwords are not stored as plain text. I encourage you to do some research before making any assumptions. |
|
I've not said that we won't implement this. But personally I will not waste time on this since only few website are using this scheme and there are core feature that need much work instead.
Never heard of strike/protest? If users don't have a way to login they should blame Santander for using that login method.
Then tell me how they are stored. The only viable option is using 2 password, one stored as hash and one stored plaintext, asking the full one and only part of the second one, but from the screenshot (and from what I read online about Santander) this is not the case I would love reading some papers/documentations on that (but sadly all banking system are closed source proprietary software) |
|
I was recently confronted with this weird confounding authentication scheme on a UEFI console when I tried to change secure boot settings. That was the one and only time I've ever had that. Never before, never since and I'm still puzzled by it. It is so astoundingly counter-intuitive that I almost forgot what password I chose when it asked me for the 3rd and 5th character of my temporary 7 character bullshit password. |
|
BTW I agree with @TheZ3ro that this is very low priority. If somebody wants to implement it, fine by me. But for us it's no priority. I consider this authentication scheme very bad practice for obvious reasons. The most obvious is its terrible usability which I described above, the other is its security. As for how banks implement this scheme, we have no idea what methods they use, because, as said before, they are all closed-source. The three supposedly most viable options would be symmetric encryption (hopefully with some sort of HSM or at least TPM), hashes of all possible combinations of letters or secret sharing where you use your partial passwords to encrypt a stored hash value which you can later compare. None of these are industry standard best practices for storing passwords. Symmetric encryption may compromise passwords if the keys are leaked. There is expensive security hardware which is designed to prevent that, but why not simply hash the passwords for free? |
|
Is this feature still going to be implemented (if not eventually)? for me its one of the biggest headaches re keepassXC. There was progress made in issue #1245 but that got closed. |
|
My opinion this feature should never be implemented, it is bad in all cases, just change the bank to another with proper security practices. |
|
please expand on "bad in all cases"; yes the banking security is potentially a little less, but i'm not moving my bank because it's hard to type in my password / the bank does not have the best practices. what harm, apart from needing a bit of coding time, does it cause to add it in? |
Usability/security.
it should not be a feature at all, as it is a bad security practice. Check BarclayCard, they are authentication a user by 6 digit pin and 2 letters from memorable information, instead of implementing 2FA as they should.
benefit of usability may be, questionable, but it will be a huge step back in security, people should stop using these banks and not move bad practices into password managers.
you should move your bank because they are incompetent.
more code => more complexity => more issues Example is 2FA software token functionality should not be implemented in password managers because it kills the idea of "the second factor", but with your logic it should be added as it "would provide a benefit to a number of people". |
|
We have already added 2FA TOTP in KeePassXC and it does not kill the idea of a second factor. You can create multiple databases and simply store your TOTP token separately from your main password database. Use a different master key and there is your second factor. In fact, I would argue this is much more secure than storing that information on a phone that only gets security updates semi-annually. As for this "feature" I do intend to implement it based on the original PR that was submitted, but not until 2.5.0. |
this is exactly the wrong 2FA usage, the attacker needs to get access only to one device to perform the attack now. there is no physical separation of factors anymore in your case.
this is why phone is just an additional factor in authentication, hacking the phone or getting access to a hardware generator is not enough to log in to a system with 2FA.
okey then, may be 'reboot' went to much into 'reboot'. |
And that's exactly why YOU lose potential users, Mr. Know-it-all. |
|
@OskarW85 that quote is not from a member of the KeePassXC team... |
|
@OskarW85 the first: these banks should loose clients, |
|
I don't know what trivial bugs you are talking about, but I object to the statement that we implement bad security practices. I am inclined to lock this issue. The discussion has derailed and is leading nowhere. |
|
I actually started working on this independently, just saw this issue now. I'll try clean up what I've got and submit a PR, unless @droidmonkey says he has it done? |
|
I haven't done it, but there are major autotype changes in my branch |
|
There is no auto type functionality in my implementation. |
|
(Yet) :p |
* Closes #725 Support Auto-Type {PICKCHARS} placeholder. Open a dialog that lets you pick characters of an entry's password by their position. Supports typing {TAB} in between characters to move between fields (if necessary). Also supports using arrow keys to quickly navigate around the choice grid.
* Closes #725 Support Auto-Type {PICKCHARS} placeholder. Open a dialog that lets you pick characters of an entry's password by their position. Supports typing {TAB} in between characters to move between fields (if necessary). Also supports using arrow keys to quickly navigate around the choice grid.
* Closes #725 Support Auto-Type {PICKCHARS} placeholder. Open a dialog that lets you pick characters of an entry's password by their position. Supports typing {TAB} in between characters to move between fields (if necessary). Also supports using arrow keys to quickly navigate around the choice grid.
* Closes #725 Support Auto-Type {PICKCHARS} placeholder. Open a dialog that lets you pick characters of an entry's password by their position. Supports typing {TAB} in between characters to move between fields (if necessary). Also supports using arrow keys to quickly navigate around the choice grid.
* Closes #725 Support Auto-Type {PICKCHARS} placeholder. Open a dialog that lets you pick characters of an entry's password by their position. Supports typing {TAB} in between characters to move between fields (if necessary). Also supports using arrow keys to quickly navigate around the choice grid.
* Closes #725 Support Auto-Type {PICKCHARS} placeholder. Open a dialog that lets you pick characters of an entry's password by their position. Supports typing {TAB} in between characters to move between fields (if necessary). Also supports using arrow keys to quickly navigate around the choice grid.
* Closes #725 Support Auto-Type {PICKCHARS} placeholder. Open a dialog that lets you pick characters of an entry's password by their position. Supports typing {TAB} in between characters to move between fields (if necessary). Also supports using arrow keys to quickly navigate around the choice grid.
|
How use this? |
|
It's done, going to be merged into 2.7.0 |
* Closes #725 Support Auto-Type {PICKCHARS} placeholder. Open a dialog that lets you pick characters of an entry's password by their position. Supports typing {TAB} in between characters to move between fields (if necessary). Also supports using arrow keys to quickly navigate around the choice grid.
* Closes #725 Support Auto-Type {PICKCHARS} placeholder. Open a dialog that lets you pick characters of an entry's password by their position. Supports typing {TAB} in between characters to move between fields (if necessary). Also supports using arrow keys to quickly navigate around the choice grid.
* Closes #725 Support Auto-Type {PICKCHARS} placeholder. Open a dialog that lets you pick characters of an entry's password by their position. Supports typing {TAB} in between characters to move between fields (if necessary). Also supports using arrow keys to quickly navigate around the choice grid.
|
They likely only have a few permutations of choices and just precompute the hash for each permutation from your original password when you set/reset it. They definitely aren't being fancy! |
|
Salted one-character passwords sound like a pretty dumb idea, because the salt is in plaintext. Should be easily crackable in milliseconds if you know the scheme. Go, try it, here's a pair of sha256 hash and salt: And since the bank also needs to keep track of which hash is which character in which position, they would have to save all 6 as a list in the correct order, so it's basically just obfuscated plaintext. |
* Closes #725 Support Auto-Type {PICKCHARS} placeholder. Open a dialog that lets you pick characters of an entry's password by their position. Supports typing {TAB} in between characters to move between fields (if necessary). Also supports using arrow keys to quickly navigate around the choice grid.
* Closes #725 Support Auto-Type {PICKCHARS} placeholder. Open a dialog that lets you pick characters of an entry's password by their position. Supports typing {TAB} in between characters to move between fields (if necessary). Also supports using arrow keys to quickly navigate around the choice grid.
* Closes #725 Support Auto-Type {PICKCHARS} placeholder. Open a dialog that lets you pick characters of an entry's password by their position. Supports typing {TAB} in between characters to move between fields (if necessary). Also supports using arrow keys to quickly navigate around the choice grid.
* Closes #725 Support Auto-Type {PICKCHARS} placeholder. Open a dialog that lets you pick characters of an entry's password by their position. Supports typing {TAB} in between characters to move between fields (if necessary). Also supports using arrow keys to quickly navigate around the choice grid.
* Closes keepassxreboot#725 Support Auto-Type {PICKCHARS} placeholder. Open a dialog that lets you pick characters of an entry's password by their position. Supports typing {TAB} in between characters to move between fields (if necessary). Also supports using arrow keys to quickly navigate around the choice grid.
|
Pickchars syntax still apparently not aligned with keepass. Produces an error: |
|
We chose not to follow that syntax. You can opt to use another attribute by name (case matters), but not the character positioning portion. Example: |

Original KeePass has {PICKCHARS} placeholders for entering partial password, would be nice if it was implemented.
Expected Behavior
When entry has {PICKCHARS} placeholder, window is opened that lets user choose which characters of the password should be entered. It looks like this in KeePass:
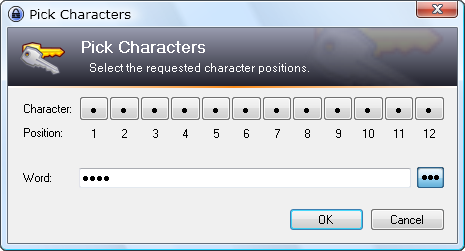
I'd gladly try to implement it myself if someone points me in the right direction :)
The text was updated successfully, but these errors were encountered: