-
Notifications
You must be signed in to change notification settings - Fork 46
Separate block confirmations #501
New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
Conversation
9e45e6a to
386000b
Compare
| account: AccountId, | ||
| amount: Amount, | ||
| shard: &ShardIdentifier, | ||
| calls: &mut Vec<OpaqueCall>, |
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
Removed this input parameter, as there will never(!) be a new OpaqueCall introduced during Stf::execute of a shielding extrsinic. (New OpaqueCall is only issued during execute when calling "unshield")
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
Thanks for clarifying this
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
Haha, good catch. 🛩️
| sp-utils = { version = "4.0.0-dev", default-features = false, git = "https://github.com/paritytech/substrate.git", branch = "master" } | ||
| sp-version = { version = "4.0.0-dev", default-features = false, git = "https://github.com/paritytech/substrate.git", branch = "master" } | ||
| sp-application-crypto = { version = "4.0.0-dev", default-features = false, git = "https://github.com/paritytech/substrate.git", branch = "master" } | ||
| #beefy-merkle-tree = { version = "4.0.0-dev", default-features = false, git = "https://github.com/paritytech/substrate.git", branch = "master", features = "keccak" } |
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
That's the ugly part here: substrate actually has a no-std compatible merkle tree primitives crate: https://github.com/paritytech/substrate/tree/master/frame/beefy-mmr/primitives
However, this was introduced on 23rd of September. We are not yet on this substrate commit. Can you agree with this temporary solution and to remove it once we are on this commit? If yes, I'll create an appropriate issue ofc.
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
If it's well documented and even has a corresponding issue, that's totally fine for me 👍
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
I think it's fine too. 👍
| @@ -0,0 +1,229 @@ | |||
| // This file is part of Substrate. | |||
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
This file was copy pasted from https://github.com/paritytech/substrate/blob/master/frame/beefy-mmr/primitives/src/lib.rs. Can be removed once we are above commit paritytech/substrate@65ac6f3
f1773ad to
5e49a19
Compare
enclave-runtime/src/lib.rs
Outdated
| let xt_block = [TEEREX_MODULE, BLOCK_CONFIRMED]; | ||
| let opaque_call = | ||
| OpaqueCall::from_tuple(&(xt_block, shard, block_hash, state_hash_new.encode())); | ||
| let opaque_call = proposed_sidechain_block_extrinsic(shard, block_hash); |
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
so we now use the sidechain block hash instead of the state hash for this extrinsic?
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
Not exactly. State hash has been removed from the extrinsic as it didn't have any use case at all (#457)
| /// Creates a proposed_sidechain_block extrinsic for a given shard id and sidechain block hash. | ||
| fn proposed_sidechain_block_extrinsic(shard_id: ShardIdentifier, block_hash: H256) -> OpaqueCall { | ||
| OpaqueCall::from_tuple(&([TEEREX_MODULE, PROPOSED_SIDECHAIN_BLOCK], shard_id, block_hash)) | ||
| } |
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
Also here, I'd prefer the create_ in front. In a future refactoring, we could put these into the extrinsics factory component or something similar?
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
Already changed. :) Yes, definitely - but I think the whole lib.rs (just like in PR #500 but also for parentchain syncing) should be refactored (but that's your call).. I didn't want to start something that will be changed in the future anyway. If you have a place they belong to already, I'll gladly move them.
enclave-runtime/src/tests.rs
Outdated
| fn empty_extrinsic_vec_gives_zero_merkle_root() { | ||
| // given | ||
| let block_hash = H256::from([1; 32]); | ||
| let extrinsics = Vec::new(); | ||
| let expected_call = | ||
| ([TEEREX_MODULE, PROCESSED_PARENTCHAIN_BLOCK], block_hash, H256::default()).encode(); | ||
|
|
||
| // when | ||
| let call = crate::processed_parentchain_block_extrinsic(block_hash, extrinsics); | ||
|
|
||
| // then | ||
| assert_eq!(call.0, expected_call); | ||
| } | ||
|
|
||
| fn some_extrinsics_vec_give_non_zero_merkle_root() { | ||
| // given | ||
| let block_hash = H256::from([1; 32]); | ||
| let extrinsics = vec![H256::from([4; 32]), H256::from([9; 32])]; | ||
| let zero_root_call = | ||
| ([TEEREX_MODULE, PROCESSED_PARENTCHAIN_BLOCK], block_hash, H256::default()).encode(); | ||
|
|
||
| // when | ||
| let call = crate::processed_parentchain_block_extrinsic(block_hash, extrinsics); | ||
|
|
||
| // then | ||
| assert_ne!(call.0, zero_root_call); | ||
| } |
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
Always nice to have tests for the changes you make 🥳
| fn hash_of<T: Encode>(xt: T) -> H256 { | ||
| blake2_256(&xt.encode()).into() |
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
This is a function that we have duplicated multiple times I believe. We should at some point put it in a primitives crate where it can be properly shared.
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
Aye.. But I didn't want to touch too much code, in fear of the rebase conflicts 😨
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
I think we should simply implement hash on the extrinsic in the api-client. 😄
 murerfel
left a comment
murerfel
left a comment
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
LGTM - and if the checks pass, it should be fine
 clangenb
left a comment
clangenb
left a comment
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
Looks good to me. 👍
| account: AccountId, | ||
| amount: Amount, | ||
| shard: &ShardIdentifier, | ||
| calls: &mut Vec<OpaqueCall>, |
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
Haha, good catch. 🛩️
| sp-utils = { version = "4.0.0-dev", default-features = false, git = "https://github.com/paritytech/substrate.git", branch = "master" } | ||
| sp-version = { version = "4.0.0-dev", default-features = false, git = "https://github.com/paritytech/substrate.git", branch = "master" } | ||
| sp-application-crypto = { version = "4.0.0-dev", default-features = false, git = "https://github.com/paritytech/substrate.git", branch = "master" } | ||
| #beefy-merkle-tree = { version = "4.0.0-dev", default-features = false, git = "https://github.com/paritytech/substrate.git", branch = "master", features = "keccak" } |
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
I think it's fine too. 👍
| if let Err(e) = validator.submit_simple_header( | ||
| validator.num_relays(), | ||
| signed_block.block.header().clone(), | ||
| block.header().clone(), |
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
nice optimization.
| fn hash_of<T: Encode>(xt: T) -> H256 { | ||
| blake2_256(&xt.encode()).into() |
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
I think we should simply implement hash on the extrinsic in the api-client. 😄
Seems to work quite well: For every parentchain block we get 20 sidechain block events.
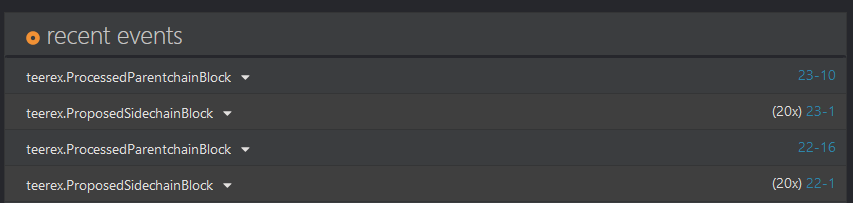
Introduces the following changes:
closes #457