-
Notifications
You must be signed in to change notification settings - Fork 35
Setup
Note: Microsoft requires that you use HTTPS for applications communicating with their authentication system. You must have your SonarQube environment working over HTTPS before you can enable this plugin.
Before starting this process, it is recommended that you first install the plugin to your SonarQube environment. You can do this from the Marketplace inside SonarQube, or download the plugin jar file directly from the releases page and place inside the extensions/plugins directory in your SonarQube installation. After installing the plugin, you need to restart SonarQube to load the plugin.
Once installed, you can register the SonarQube application in your Azure Active Directory to gather the values needed to configure and enable AAD authentication.
It is important to decide if you are going to be authenticating in a single tenant or a multiple tenant style.
A single tenant setup restricts login via Azure Active Directory to only those users that have accounts in or are guests in your Azure environment. This is the most common configuration and is the default for the plugin.
A multi-tenant setup allows users in different Azure Active Directories to authenticate and login to your SonarQube installation. This can be useful if, for example, you have contractors or customers that have their own Azure setup and want to login with these accounts. Group sync and national cloud support will not work with this setup.
-
Sign into the Azure Management Portal. (If you are using one of the "national cloud" Azure instances, log in using the correct portal URL for your country.)
-
Open the Azure Active Directory blade from either the shortcut on the left sidebar or search in the search box at the top.
-
Inside the blade, select
Propertiesfrom the Manage category and copy down the "Tenant ID". You will enter this in the plugin settings.
Note: In a multi-tenant configuration, anyone with an Azure login can authenticate, so you will need to take additional measures inside SonarQube to secure information there.
No steps are needed on the Azure Management Portal for a multi-tenant setup.
Note: While the below steps were current when written, the Azure Portal changes frequently. If things look different to you, you can reference the official docs linked at the end of this section for guidance.
-
To begin, sign into the Azure Management Portal. (If you are using one of the "national cloud" Azure instances, log in using the correct portal URL for your country.)
-
Open the Azure Active Directory blade from the shortcut on the left sidebar or search in the search box at the top.
-
On the sidebar, under the Manage category, choose
App registrationsand then selectNew registrationfrom the top bar. -
Fill in the form that appears and click the "Create" button once done.
a.
Nameshould be the name of your application. It may be shown to users in some cases, so pick something like "SonarQube" or "MyCompany SonarQube".b.
Supported account typescan be set to any option based on if you want to support multi-tenant logins or not. This can be changed later, so it is safe to start with the option for "Single Tenant"c.
Redirect URIshould be set to "Web" in the dropdown. For the URL field, you will put in the special authentication URL for this plugin. This URL is your main SonarQube URL with "/oauth2/callback/aad" at the end. For example, if your main URL is "https://sonarqube.example.com/", you would enter "https://sonarqube.example.com/oauth2/callback/aad".Once these are filled out, you can click
Registerto register the application. -
When the registration is complete, you should be taken to a screen with information on the new application. Copy down the "Application (client) ID", it's used as the "Client ID" in the plugin settings.
-
Choose
Authenticationfrom the sidebar. In the section titled "Implicit grant and hybrid flows", look for the option titled "ID tokens (used for implicit and hybrid flows)" and check the box labeled. ClickSaveto save this change. -
Click on
Certificates & secretsfrom the sidebar and click onNew client secret. You can type anything you want in the "Key Description" field. Select the expiration length you want. Keep in mind that longer expiration times will lower security. Once done, clickAdd. Once the process finishes, you will see the new secret on the screen. Copy data for the "Value", it's used as the "Client Secret" in the plugin settings.
For more details on the application creation procedure, you can reference the Microsoft document How to: Use the portal to create an Azure AD application and service principal that can access resources
If you have not installed the plugin yet, you will need to do so before you continue with these steps.
Note: Each setting has its own save button when you modify it. Make sure to click the "Save" button after you change each setting.
-
Log into your SonarQube install with a local account that has administrative permission.
-
Make sure you have set Server base URL under Settings/General to the root of the SonarQube installation without a trailing slash (For example http://sonarqube.yourdomain.com).
-
Click on the
Administrationheader at the top, then select theAzure Active Directorytab from the general settings area. If you do not see this section, ensure the plugin is installed and that you have restarted SonarQube to load the plugin. -
Fill in the
Client IDandClient Secretfields with the values you copied down from the Azure Management Portal. -
This step varies depending on if you are installing single or multiple tenant:
Single-tenant: If you are setting up SonarQube as a single tenant application, fill in the
Tenant IDfield with the value you copied down.Multi-tenant: If you are setting up as a multi-tenant application, toggle the setting labeled
Multi-tenant Azure Applicationto on/enabled. -
Toggle the setting labeled
Enabledto on/enabled to activate the plugin.
At this point, any users on your Azure Active Directory can sign in to SonarQube. The login page will have changed slightly, looking much like the image:
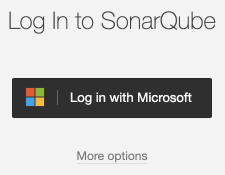
A new button labeled "Log in with Microsoft" will allow users to use AAD to log in. The username and password fields for local accounts are now behind a link labeled "More options".
This plugin supports group synchronization with your Azure Active Directory. If you want to set this up, you can look at the documentation on Group Synchronization.