-
Notifications
You must be signed in to change notification settings - Fork 9.5k
New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
terraform modules value of count cannot be computed #12570
Comments
|
I've seen a similar problem. There seems to be a general issue where the deferred evaluation of the Here's my case: Module source: If I do this, I get: However, if I simply change the My current workaround is to declare a Provisioner: |
|
I was just hit with a similar problem: Throws a circular dependency error: But if I hard code a Thanks for the workaround @mfischer-zd. It's not pretty but seems we have no choice at the moment. |
|
It look like all of the calculated parameters that influence the |
|
I think I have a similar problem, it seems like my count worked when I had but when I added this (👇) ternary expression, it doesn't work when |
|
We're having this issue as well, similar to the initial report (trying to pass an iam policy document into a module that references resources outside the module). If the resources already exist then it seems to work (in our staging environment the resources were created in one update and the policy added in a subsequent one, which worked), but if the resources don't exist (as we found in our production environment where both updates were applied at once) then we get the |
|
I'm facing a similar issue with terraform version 0.9.6 as well The weird thing is that im using this in one module and it seems to be working fine there, the same expression in another module with another variable inside results in the Another thing that confuses me is that, I changed the line to And it worked for the first time after doing this, no errors everything created successfully, but after that time, doing this also results in the same error. Is there a workaround to this? |
|
apparently I changed to (another variable) and it is not complaining (for now) |
|
This is still a bug / problem with Here is my version the error from a VPC module's test env: |
|
duplicate of #10857 |
|
While I can understand the choice to not allow This fails if the Issues like this make it difficult to use Terraform modules. |
|
Hi all! Thanks for the great discussion here. The current approach was added as a compromise to enable the use of data source results to be used in Something like #4149 will be the eventual solution to this. This sort of workflow/architecture change we want to approach carefully, but we do intend to address this problem once we've worked though the implications and found a solid design for it. |
|
What exactly is the current approch? I'm using an external data source which massages some of my input from what is realtively easy for humans to configure, to what is relatively easy to express in terraform, and count doesn't seem to like the result of it. My external data source only reads in data that has been passed as input variables. i've tried this in both Terraform 0.9.9 and 0.9.11. |
|
The current constraint is that
@rorybrowne if your |
|
Thanks @apparentlymart I tried to reproduce it with a sample that I could send, but the reproduction didn't work. Some detective work later, it turned out that my external resource had some syntax errors. Having that said, it would've been nice if I got a "your external data resource is fu...barred", rather than a "you can't use count" type error message. I'll see if I can recreate that problem ( unfortunatly I didn't take a commit at the time ), and do up a bug report. |
|
@apparentlymart Thanks for taking the time to explain these proposed approaches. To me using the -target manually means that doing this at scale becomes unwieldy. Is there any update on when this is expected to be automated? Issue 4149 doesn't seem to have much activity. |
|
I'm really baffled by the behaviour of Initially I tried to pass in the output from another pre-existing module: which raises this error on Then I tried splitting this into two separate resources and referencing the existing module's output as remote state: but received the same error. And then out of frustration I tried using a literal list: And still get the same error: So at this point it looks to me like you either can't use a ternary expression in a So is this broken? Are the docs wrong? Or am I missing something? Because with this current behaviour it's not clear what the intention behind the Terraform module registry is, if passing output from one module to the input of another causes problems with basic constructs like |
We need to work around hashicorp/terraform#12570 JIRA: PLAT-1117
This is now required to work around hashicorp/terraform#12570 JIRA: PLAT-1117
The way in which we use the 'lb' and 'node_group' modules, the `instance_target_group_arns` value is the output of the lb module. We tried using the length of the value in a count parameter which is not supported by Terraform (because it's computed). There are some issues in the Terraform project regarding this limitation, for instance: hashicorp/terraform#12570 In some cases it's recommended to use `-target` when applying Terraform changes to create the LB resources before the node_group, but this is quite difficult to integrate in our solution because we don't have a proper CD pipeline yet. At this point, our way of getting around this issue is by creating a `_length` variable with the expected length of instance_target_group_arns, that we calculate outside the module. This is aligned with the solution used with private networks and NAT instances in `terraform/modules/aws/network/private_subnet/main.tf`.
The way in which we use the 'lb' and 'node_group' modules, the `instance_target_group_arns` value is the output of the lb module. We tried using the length of the value in a count parameter which is not supported by Terraform (because it's computed). There are some issues in the Terraform project regarding this limitation, for instance: hashicorp/terraform#12570 In some cases it's recommended to use `-target` when applying Terraform changes to create the LB resources before the node_group, but this is quite difficult to integrate in our solution because we don't have a proper CD pipeline yet. At this point, our way of getting around this issue is by creating a `_length` variable with the expected length of instance_target_group_arns, that we calculate outside the module. This is aligned with the solution used with private networks and NAT instances in `terraform/modules/aws/network/private_subnet/main.tf`.
|
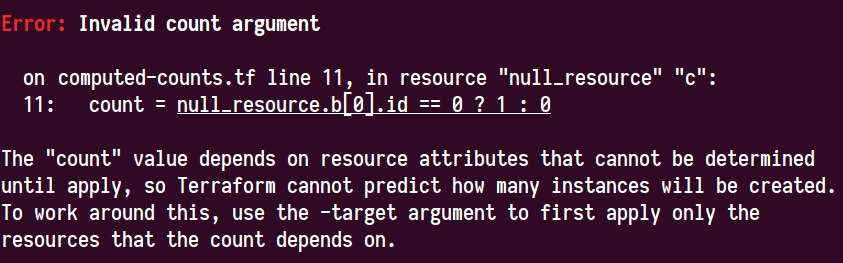
Hi all! By now this issue is covering quite a number of different root problems that all happen to have the same symptoms. The root problem that Terraform cannot support a computed For example, several people in this thread were (understandably) surprised that Terraform would consider an expression like resource "null_resource" "a" {
count = 2
}
resource "null_resource" "b" {
count = length(null_resource.a)
}
output "ids" {
value = null_resource.b.*.id
}Note that the terminology "computed" has now been replaced with "unknown" in v0.12, with unknown values showing as "(known after apply)" in the rendered diff. Along with this specific case, a list or map that contains an unknown element can now pass through a module boundary (in via a variable or out via an output) as-is, without the entire collection itself becoming unknown as we saw in v0.11 and prior. The appearance of this error should therefore be in a much smaller set of cases than before. The v0.12.0-alpha1 also includes a more detailed error message for the remaining cases where count is unknown. In a future minor release we also intend to make this do one more level of analysis to find the specific reference that is unknown and indicate it directly, ideally also then offering an exact |
|
I have figured out a workaround for # Compute dynamic dependencies for RKE provisioning step (workaround, may be not needed in 0.12)
locals {
rke_cluster_deps = [
"${join(",",module.master.prepare_nodes_id_list)}",
"${join(",",module.worker.prepare_nodes_id_list)}",
"${join(",",module.master.associate_floating_ip_id_list)}",
"${join(",",module.master.allowed_ingress_id_list)}",
"${join(",",module.worker.allowed_ingress_id_list)}",
"${join(",",module.secgroup.rule_id_list)}",
"${module.network.interface_id}",
]
}
# Provision RKE
resource rke_cluster "cluster" {
nodes_conf = ["${concat(module.master.node_mappings,module.worker.node_mappings)}"]
bastion_host = {
address = "${element(module.master.public_ip_list,0)}"
user = "${var.ssh_user}"
ssh_key_path = "${var.ssh_key}"
port = 22
}
ignore_docker_version = "${var.ignore_docker_version}"
# Workaround: make sure resources are created and deleted in the right order
provisioner "local-exec" {
command = "# ${join(",",local.rke_cluster_deps)}"
}
}
# Write kubeconfig.yaml
resource local_file "kube_cluster_yaml" {
filename = "./kubeconfig.yml"
content = "${rke_cluster.cluster.kube_config_yaml}"
}I do this mostly because I want |
|
Hey Mcapuccini, I'm also using rancher and trying (hard) to create some valid and dynamic yaml (I'm trying to use hostname). I'm not using ansible so my config may differ from yours. Can you offer any support at all? |
|
Hi @tim-baker115. I got it working eventually: https://github.com/mcapuccini/terraform-openstack-rke. It's still work in progress, but feel free to give it a try. If you have any problem you can come back to me via issue. I am not creating the YAML, but I am using: https://github.com/yamamoto-febc/terraform-provider-rke. |
|
For me I am literally using the example the terraform doc uses and it is failing with the "count can not be computed error": |
|
@apparentlymart I'm hitting the symptoms described in this issue, but I'm not sure the root cause is the same as what the workarounds suggested above indicate. Given the following config: resource "azurerm_app_service" "backend" {
# omitted for brevity
}
resource "azurerm_postgresql_server" "transferapi-db" {
# omitted for brevity
}
locals {
db_ip_whitelist = ["${split(",", azurerm_app_service.backend.possible_outbound_ip_addresses)}"]
}
resource "azurerm_postgresql_firewall_rule" "db-backend" {
count = "${length(local.db_ip_whitelist)}"
name = "backend"
depends_on = ["azurerm_app_service.backend", "azurerm_postgresql_server.db"]
resource_group_name = "${azurerm_resource_group.backend.name}"
server_name = "${azurerm_postgresql_server.db.name}"
start_ip_address = "${element(local.db_ip_whitelist, count.index)}"
end_ip_address = "${element(local.db_ip_whitelist, count.index)}"
}I expect to fail in the ways mentioned above when the app service is not yet provisioned. However, I'm seeing this error even after first creating the app service using I can also verify that the property is indeed known and present in my state, by looking at $ terraform state show azurerm_app_service.backend | grep possible
possible_outbound_ip_addresses = <a redacted comma-separated list of addresses>So if this is present in my state, why can I've also tried inlining the expression instead of having it in a local variable, but that made no difference. |
We have to pass the number of subnets around (rather than dynamically counting them) because of an issue in Terraform: hashicorp/terraform#12570 Without this we see the following error message when `terraform apply`ing from scratch: ``` Error: Error refreshing state: 1 error(s) occurred: * module.hsm.data.aws_subnet.vpc: data.aws_subnet.vpc: value of 'count' cannot be computed ``` If the cluster has already been spun up and the HSM module included at a later date then the Terraform would apply cleanly in its current state. This may be end up being resolved in Terraform 0.12 when it is released.
|
yesterday, terraform v0.12 is announced, but seems still doesn't support Is it true? |
|
@ozbillwang if you're looking for count in modules then check this issue #953. Its not in 0.12. |
|
Hi all, Per the earlier comment from @apparentlymart, Terraform 0.12 includes an improved error message for this situation that includes a more detailed description of the problem and a specific suggestion for how you might work around it. In the long term we'd like to make Terraform handle this situation automatically by automatically excluding the necessary resources from the initial plan, but that is already covered by #4149 and so we're going to close this one now to consolidate the discussion over there. Thanks for the great discussion here! |
|
I'm going to lock this issue because it has been closed for 30 days ⏳. This helps our maintainers find and focus on the active issues. If you have found a problem that seems similar to this, please open a new issue and complete the issue template so we can capture all the details necessary to investigate further. |
I was using terraform modules for IAM user creation, add multiple inline policies and multiple policy_arn's to the user after creation. But now I got an issue where I create an IAM_POLICY and get the arn of this policy and i am trying to add it as
policy_arn ="{module.policy.policy_arn}"but i was getting the error, value of 'count' cannot be computed.My current version of terraform is
0.8.7module/user/users.tf
module/policy/policy.tf
main.tf
when i do terraform plan i was getting the error the aws_iam_user_policy.user_policy: value of 'count' cannot be computed.
now i am not sure. how would i get the arn of the policy created in other module to the current policy_arn to the user.
I tried with
terraform 0.9.0 devits showing the same issue. but if i first apply with target module on the policy then apply for user, Its not throwing any count error. Its working. I might need a way to tell terraform to apply policy module first then apply user module. It should be done with depends_on but i'm not able to call depends_on on other modules. Could we write a null_resource depending on policy and user module depending on null_resource ?Any suggestions/workarounds or modifications to my modules will be appreciated. thanks.
The text was updated successfully, but these errors were encountered: