SIEM stands for Security Information and Event Management. It is a type of software platform that helps organizations collect, analyze, and manage security-related data from different sources within their IT infrastructure.
SIEM systems collect and analyze data from various sources, such as network devices, servers, and security logs, to identify potential security threats. The aim is to provide organizations with a comprehensive security overview, improve incident response time, and ensure compliance through detailed security reports and audit logs.
So after learning, it was time for execution - so I setup my own simple SIEM for an Azure VM to monitor RDP attacks on it! And while creating this, got to learn a lot.
Came to know about Azure Sentinel -
Azure Sentinel is a cloud-native Security Information and Event Management (SIEM) service provided by Microsoft. It is a next-generation security information and event management (SIEM) tool that is designed to help organizations monitor, detect, investigate, and respond to security threats across their entire IT environment.
Azure Sentinel is built on top of the Azure platform and uses machine learning and AI algorithms to analyze data from a variety of sources such as network traffic, security logs, and other data sources. The system is designed to be highly scalable and can handle large volumes of data.
Azure Sentinel can help in:
- Monitor and detect security threats in real-time
- Conduct investigations into security incidents using advanced analytics
- Automate security response actions to quickly contain and mitigate threats
- Integrate with other Microsoft and third-party security tools to provide a holistic view of the security environment
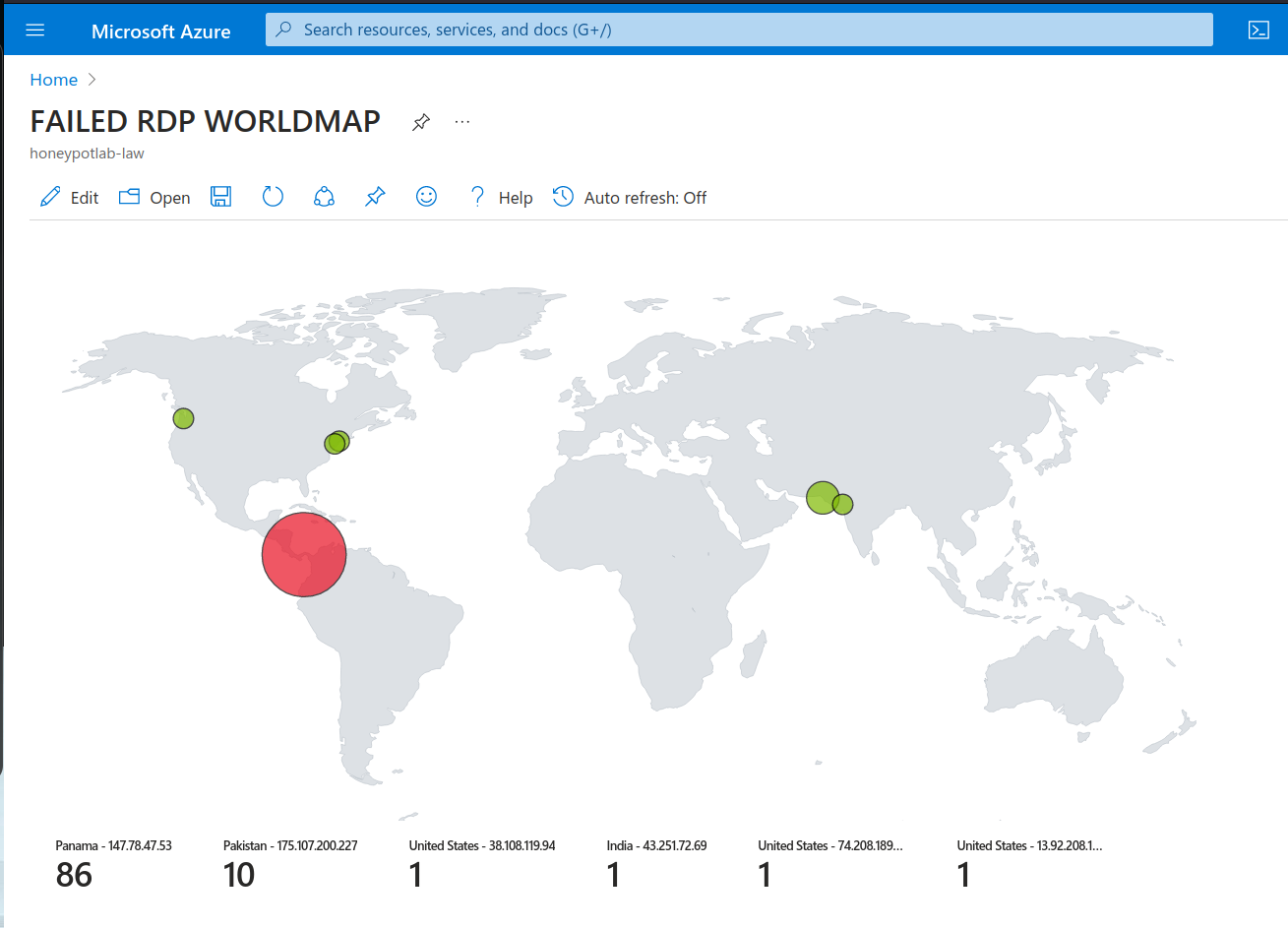
Therefore I found Sentinel to be perfect for my use. On top of it, I used powershell scripting, and IP Geolocation to mark the attack sources on a map.
During the building phase, I performed the following tasks:
- Used custom PowerShell script to extract metadata from Windows Event Viewer to be forwarded to third party API in order to derive geolocation data
- Configured Log Analytics Workspace in Azure to ingest custom logs containing geographic information (latitude, longitude, state/province, and country)
- Configured Custom Fields in Log Analytics Workspace with the intent of mapping geo data in Azure Sentinel
- Configured Azure Sentinel (Microsoft's cloud SIEM) workbook to display global attack data (RDP brute force) on world map according to physical location and magnitude of attacks.
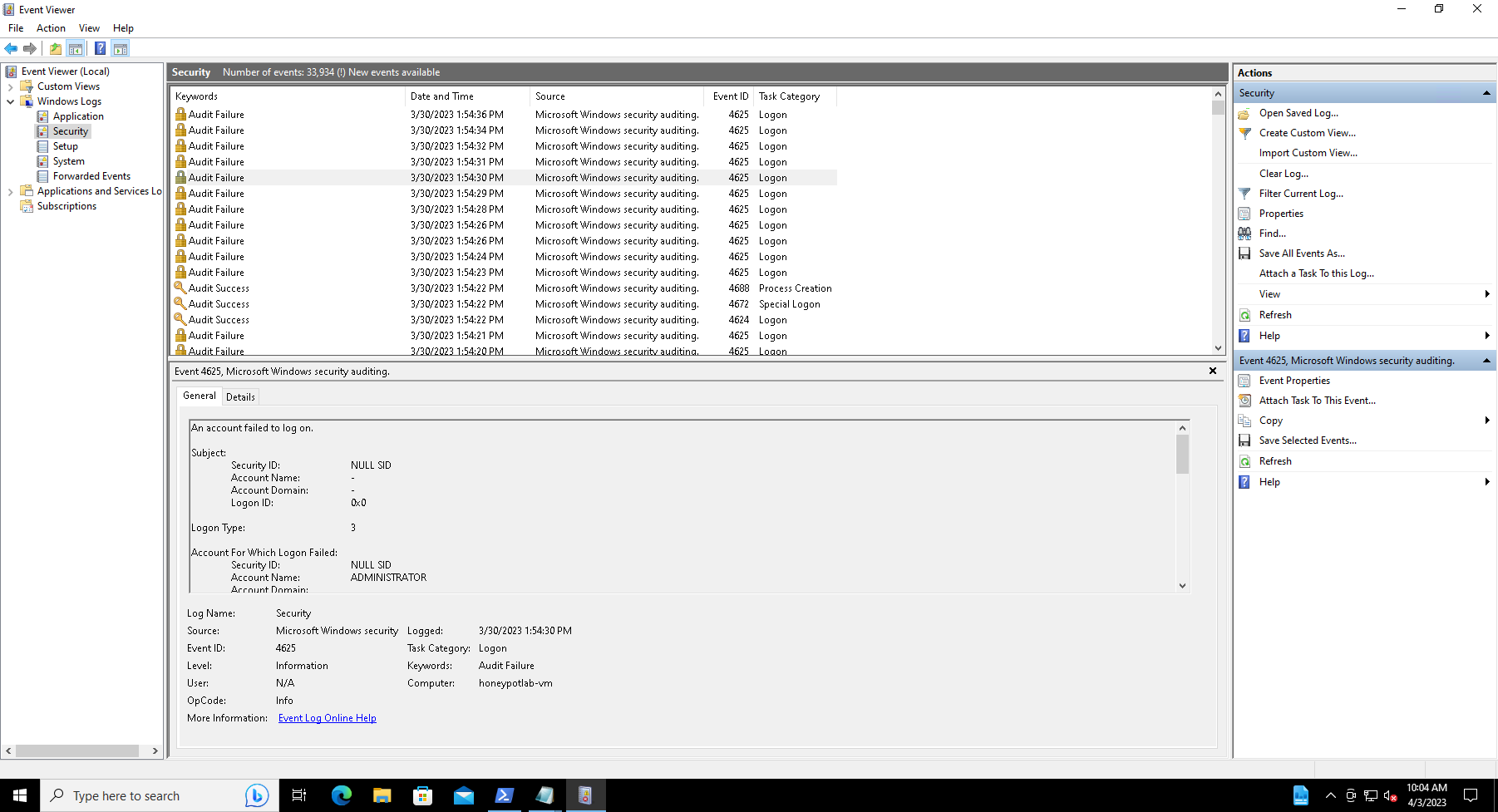
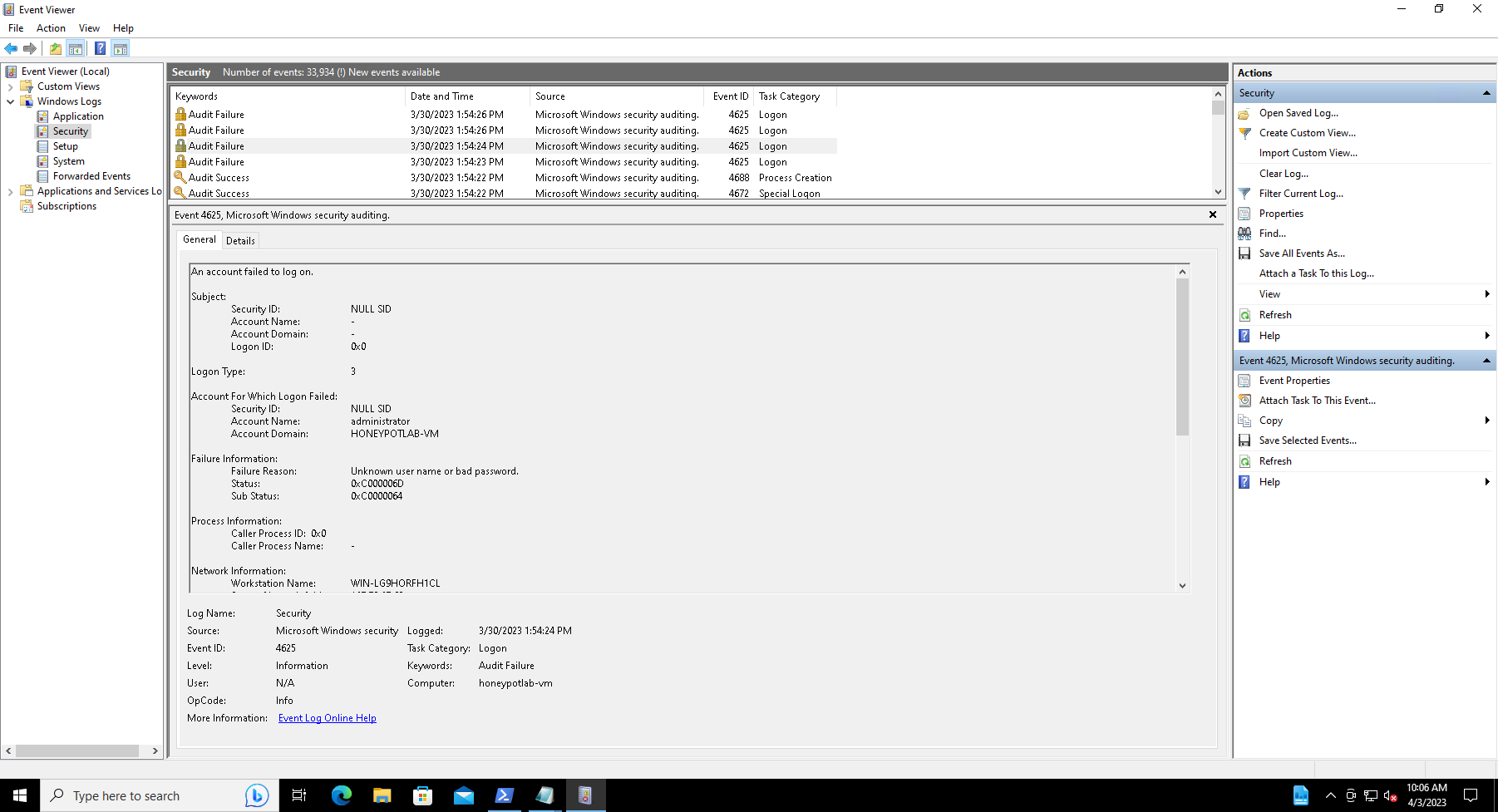
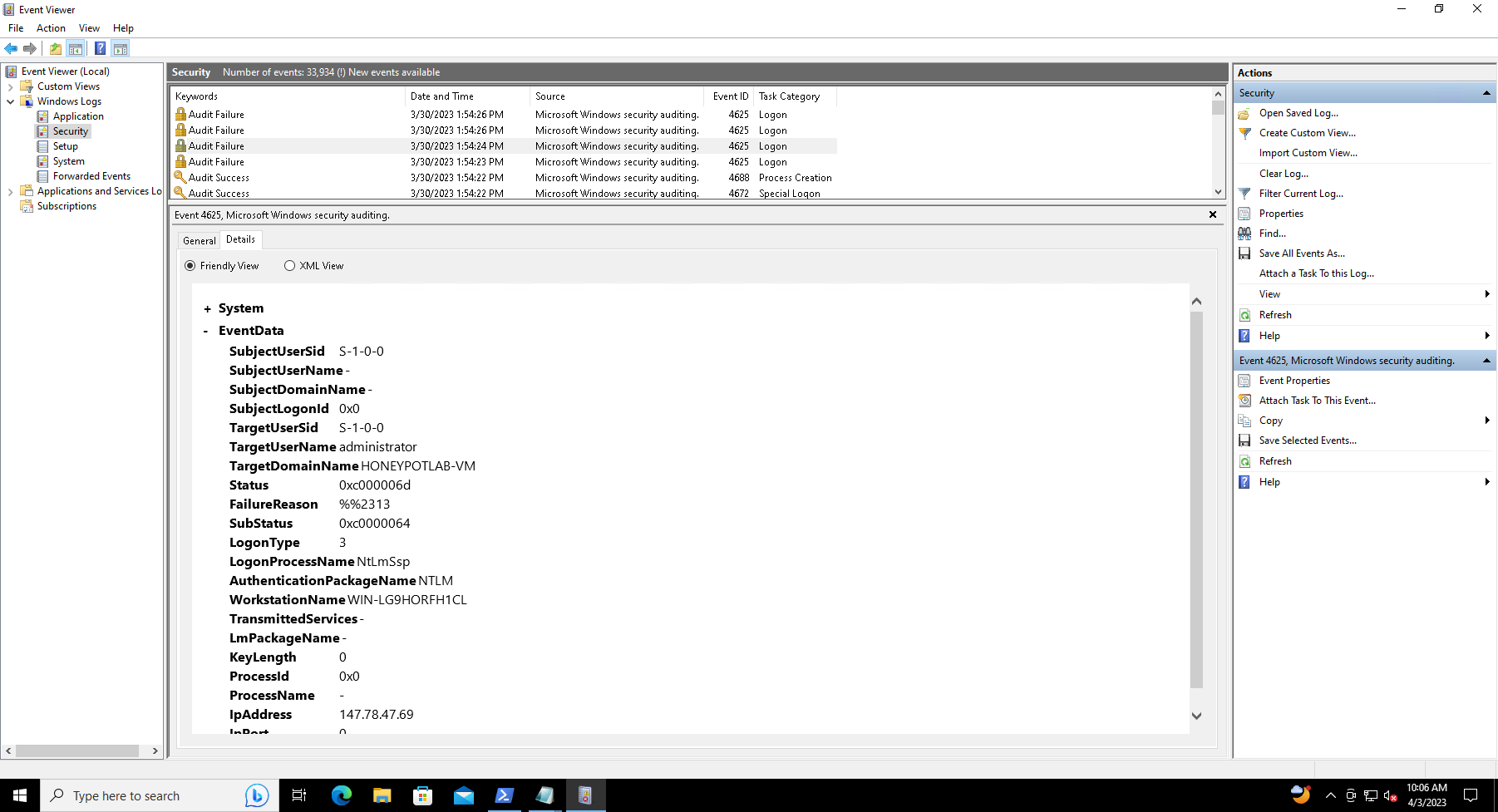
This PowerShell code is designed to retrieve information about failed Remote Desktop Protocol (RDP) logons from Windows Event Viewer in real-time, using a filter to select events of interest. This script uses the API provided by ipgeolocation.io to get the geolocation data for the IP address of the user who made the login attempt.
After detecting a failed RDP event, the script extracts necessary fields from the event and combines them with the retrieved geolocation data to create a log entry. Before the log entry is added to the custom log file, the script checks if there are any duplicates. The log consists of details like destination host, username, source host, state, country, label, and timestamp. If a duplicate is found, it skips that entry.
The script also ensures that enough sample log files are created beforehand to train the Extract feature in Log Analytics workspace.
$API_KEY = "YOUR-API-KEY-HERE"
$LOGFILE_NAME = "failed_rdp.log"
$LOGFILE_PATH = "C:\ProgramData\$($LOGFILE_NAME)"
-
$API_KEYis set to a string value that is the API key for use in some kind of application or script. -
$LOGFILE_NAMEis set to a string value that represents the name of the log file that will be generated by the script. -
$LOGFILE_PATHis set to a string value that represents the path where the log file will be saved. The path includes the$LOGFILE_NAMEvariable, which has been concatenated using "string interpolation" i.e the$()syntax. So, this line of code is equivalent toC:\ProgramData\failed_rdp.logwhich is the full path for the logfile.
The code defines a PowerShell function called write-Sample-Log() that writes a log string to a file at the location specified by the $LOGFILE_PATH variable. The log string contains comma-separated key-value pairs, each describing some aspect of an event, likely related to something like a network connection or user activity.
The Out-File cmdlet is used to append the log string to the specified file ($LOGFILE_PATH) using UTF-8 encoding. The -Append parameter tells the cmdlet to add the output to the end of the file instead of overwriting it.
Script retrieves failed login attempts from the Windows Event Viewer logs and creates a custom log file with additional information about each failed attempt, including geolocation data for the IP address associated with the failed attempt.
The script starts with an infinite loop using the $true variable. Within this loop, it retrieves events from the Event Viewer logs based on a filter defined in an XML file specified by $XMLFilter, using the Get-WinEvent cmdlet. If there are no errors returned while retrieving events, the script then steps through each event collected from the logs using a foreach loop.
For each event, the script extracts information from the event related to the failed login attempt, such as the timestamp, machine name, attempted username, and source IP address. It then checks if the length of the source IP address is greater than or equal to 5 characters, implying the presence of an IP address value. If the IP address exists, the script prepares a timestamp and various other values related to the event, such as the destination host, username, and source host.
Next, it checks the content of an existing log file at location $LOGFILE_PATH to ensure that the log entry isn't already present. If there is a new log entry to be created, the script uses the IP geolocation API provided by ipgeolocation.io to retrieve latitude, longitude, state, and country data associated with the IP address of the failed login attempt. It then creates a new line in the custom log file at $LOGFILE_PATH that contains all the extracted information about the failed login attempt, including the geolocation data.
Finally, the script outputs a formatted message to the console indicating the successful addition of the new log entry, containing the same information that was added to the custom log file. The script repeats this process indefinitely, sleeping for 1 second between polls of the Event Viewer logs, until it is manually stopped or the script host is shut down.