-
Notifications
You must be signed in to change notification settings - Fork 8.5k
[ML] Adds security_linux and security_windows Modules #85065
New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
Conversation
refactored multi-index, multi-pipeline jobs for 7.11. These are new modules that will live alongside the existing jobs.
|
Pinging @elastic/ml-ui (:ml) |
|
Would you be willing to add the two new modules here @randomuserid? This will ensure they show up within the Security Solution ML UI 🙂 |
added new module names to the list
|
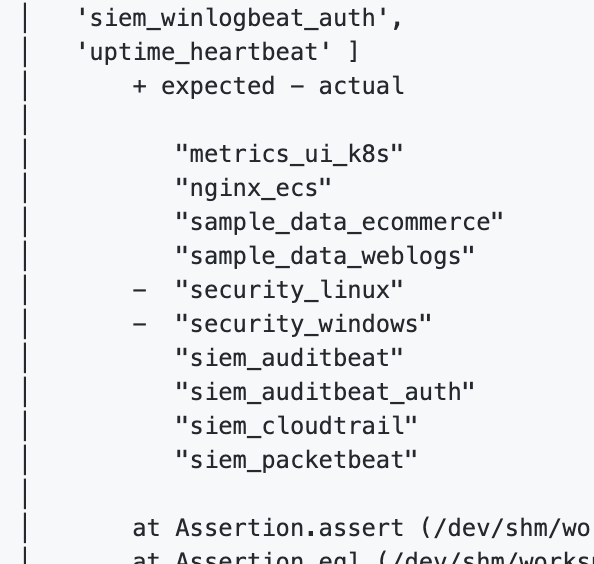
For your failing tests, add your new modules here: kibana/x-pack/test/api_integration/apis/ml/modules/get_module.ts Lines 13 to 35 in 6d12c68
FTR Failure: |
added new module names
done |
x-pack/plugins/security_solution/public/common/components/ml_popover/ml_modules.tsx
Outdated
Show resolved
Hide resolved
|
Looks like our If that's the expected behavior, you can add it to the expected |
I'm not familiar enough with these tests to understand this comment. The security_linux module was tested with both endpoint and auditbeat data although it should work with any Linux events in ECS format. Expected result is the jobs in the module can make use of any such data including data from beat / endpoint releases at the time of this writing. |
The recognizer tests verifies the modules that are detected for a dataset. This is what the UI would offer when the user selects a dataset for job creation in the ML UI. In this case, the
This should only happen if the detected module is running ok on the selected dataset. But your description sounds like the new |
|
I suspect the primary method of creating the security module jobs will be through the Security plugin UI, but if the user goes in via the ML job wizard using the
|
|
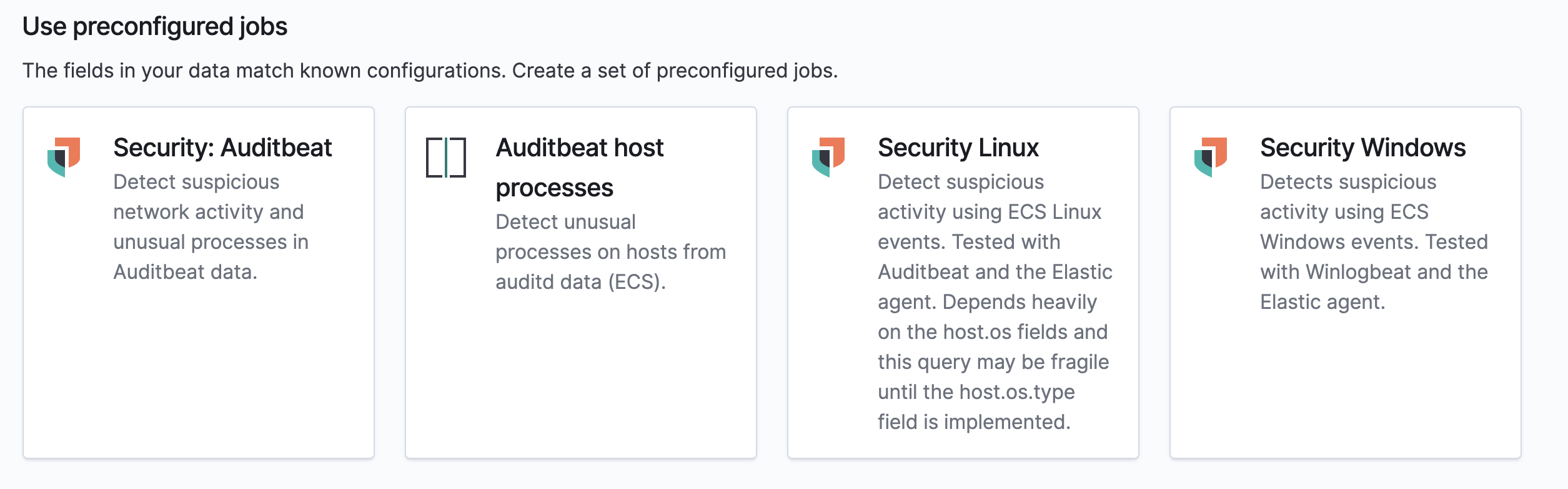
Given what @peteharverson and @pheyos pointed out, we will want to make the titles and descriptions as clear as possible. Currently, an index pattern that contains endpoint and auditbeat data (for example) will show the following cards:
|
added colon char to the module name and shortened the description
after talking with the security team today, adding this suggested text to the beginning of the description so it will tend to be visible to the user: "This is a new refactored job which works on ECS compatible events across multiple indices."
.../server/models/data_recognizer/modules/security_linux/ml/v2_linux_rare_metadata_process.json
Show resolved
Hide resolved
.../ml/server/models/data_recognizer/modules/security_linux/ml/v2_linux_rare_metadata_user.json
Outdated
Show resolved
Hide resolved
...dels/data_recognizer/modules/security_windows/ml/v2_windows_anomalous_path_activity_ecs.json
Show resolved
Hide resolved
.../data_recognizer/modules/security_windows/ml/v2_windows_anomalous_process_all_hosts_ecs.json
Show resolved
Hide resolved
...ver/models/data_recognizer/modules/security_windows/ml/v2_windows_rare_metadata_process.json
Show resolved
Hide resolved
...server/models/data_recognizer/modules/security_windows/ml/v2_windows_rare_metadata_user.json
Show resolved
Hide resolved
.../server/models/data_recognizer/modules/security_linux/ml/v2_linux_rare_metadata_process.json
Show resolved
Hide resolved
.../ml/server/models/data_recognizer/modules/security_linux/ml/v2_linux_rare_metadata_user.json
Show resolved
Hide resolved
...ver/models/data_recognizer/modules/security_windows/ml/v2_windows_rare_metadata_process.json
Show resolved
Hide resolved
...server/models/data_recognizer/modules/security_windows/ml/v2_windows_rare_metadata_user.json
Show resolved
Hide resolved
changes to the metadata jobs to make influencers identical to the originals
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
updated influencer lists match 👍 where have we settled on naming? Do we still want to use a v2 prefix or should we go with a more descriptive indicator, such as endpoint ?
Talked with the security team again on Tuesday and I added a sentence to the description, at their suggestion, rather than changing names. The prefix "endpoint" is not ideal because that could give the impression they are meant for some particular endpoint events when what we want people to take away is the fact that they are highly portable across data sources and not intended for any particular data type. After a number of conversations with the security team, no one has yet identified a naming convention that anyone likes. At their suggestion, I added the first sentence to the description instead which is expected to be more informative to users than any naming convention conceived this far. |
 peteharverson
left a comment
peteharverson
left a comment
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
Tested latest edits and LGTM
 panbalag
left a comment
panbalag
left a comment
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
LGTM
 spong
left a comment
spong
left a comment
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
LGTM! Thanks for wiring this up with the security app as well @randomuserid! 🙂
changes to two datafeeds needed for logic in the Security app - added the suffix "_ecs" to two ids.
|
In testing with @randomuserid we noticed the following two jobs wouldn't start within the Security UI as their datafeed ID's did not match their job names (were missing the
@randomuserid updated the datafeed ID's to match in 8e8372a, and I pulled the latest and verified functionality in both the Security UI and ML UI. Thanks for pairing on this Craig! 🙂 |
💛 Build succeeded, but was flaky
Test FailuresChrome X-Pack UI Functional Tests.x-pack/test/functional/apps/ml/data_frame_analytics/feature_importance·ts.machine learning data frame analytics total feature importance panel and decision path popover binary classification job should display the feature importance decision path in the data gridStandard OutStack TraceMetrics [docs]Async chunks
Distributable file count
History
To update your PR or re-run it, just comment with: |
* initial commit refactored multi-index, multi-pipeline jobs for 7.11. These are new modules that will live alongside the existing jobs. * Update ml_modules.tsx added new module names to the list * Update get_module.ts added new module names * Linter fixes * Order matters * manifest fixes added colon char to the module name and shortened the description * additon to description after talking with the security team today, adding this suggested text to the beginning of the description so it will tend to be visible to the user: "This is a new refactored job which works on ECS compatible events across multiple indices." * Adjust module recognizer test for auditbeat dataset * influencers changes to the metadata jobs to make influencers identical to the originals * change for security app changes to two datafeeds needed for logic in the Security app - added the suffix "_ecs" to two ids. Co-authored-by: Garrett Spong <[email protected]> Co-authored-by: Robert Oskamp <[email protected]> Co-authored-by: Craig Chamberlain <[email protected]> Co-authored-by: Robert Oskamp <[email protected]>
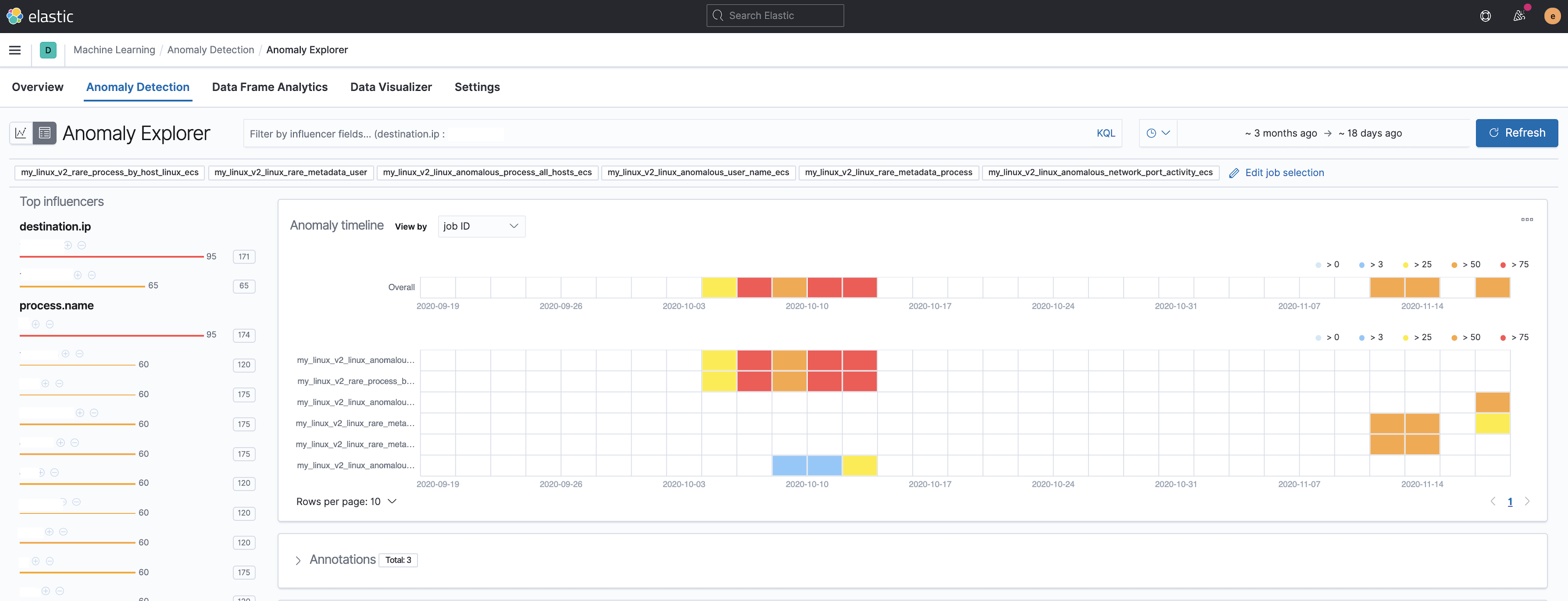
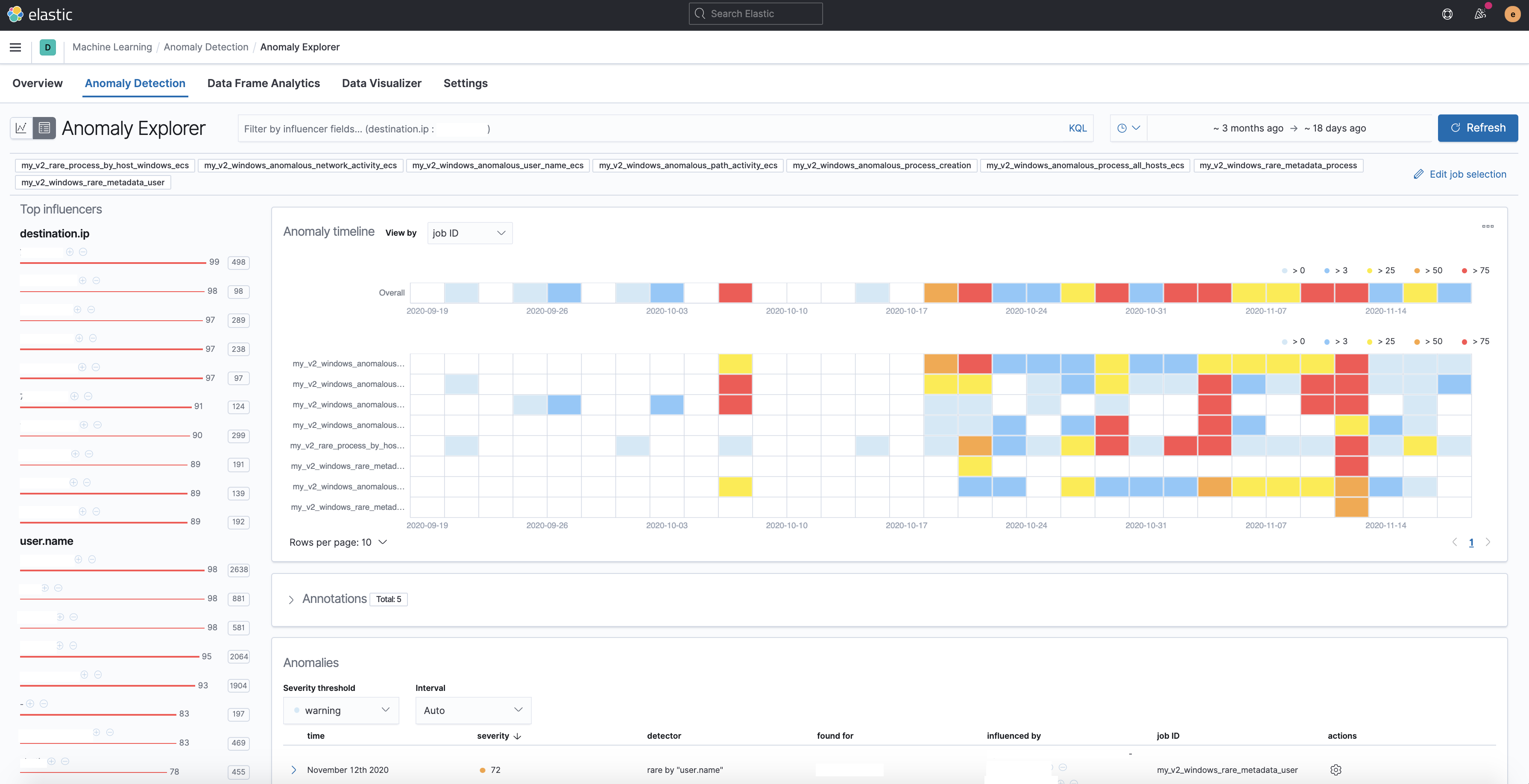
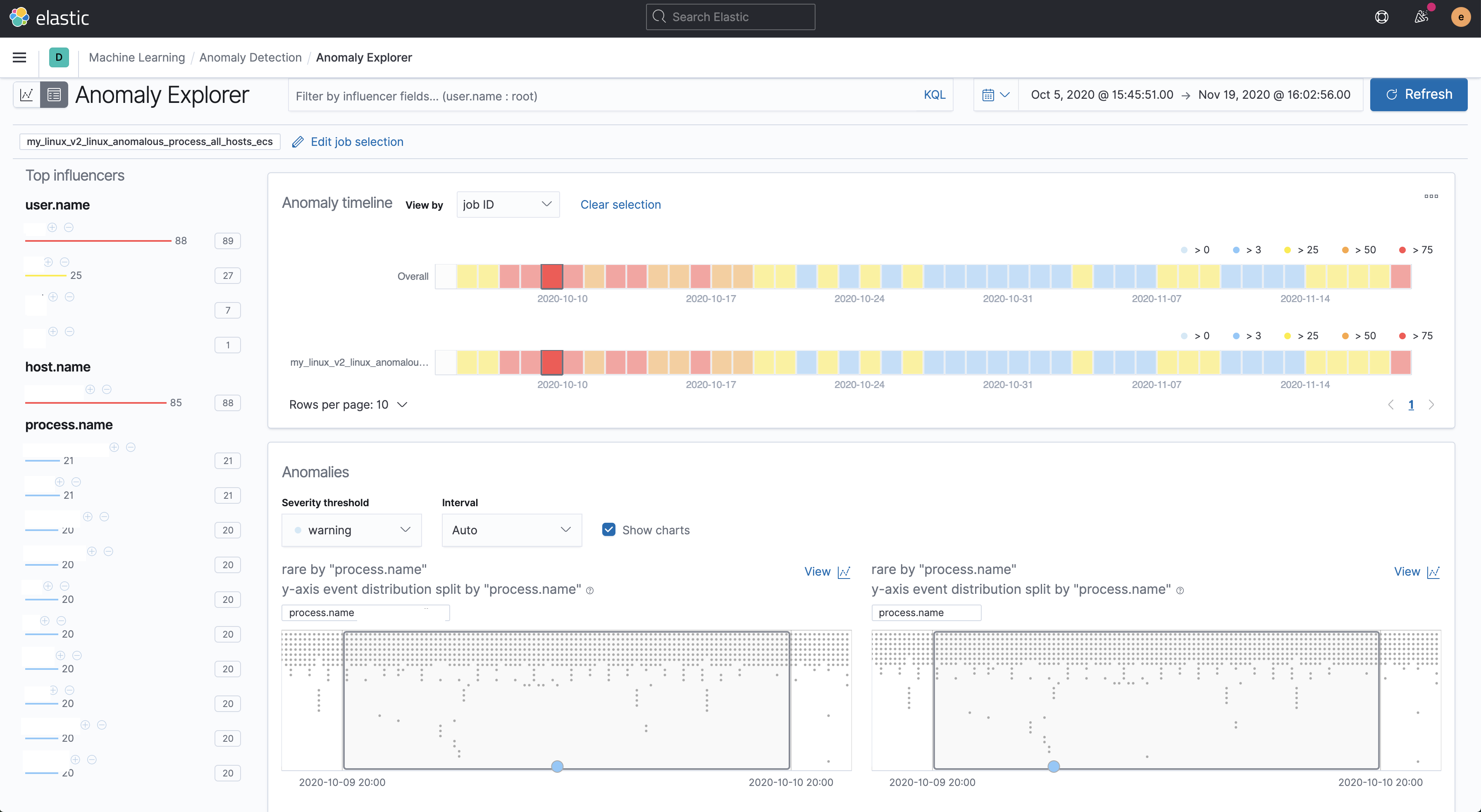
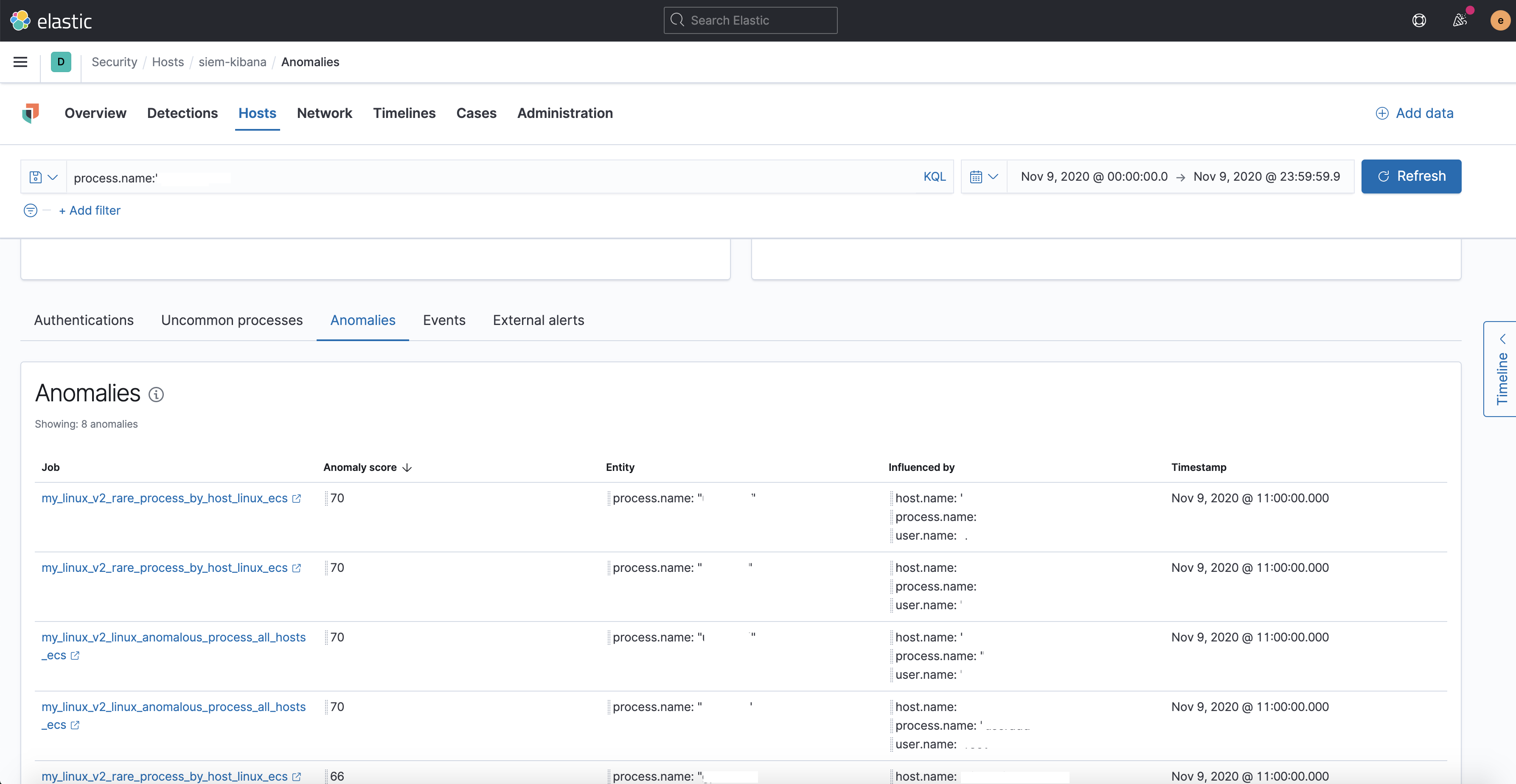
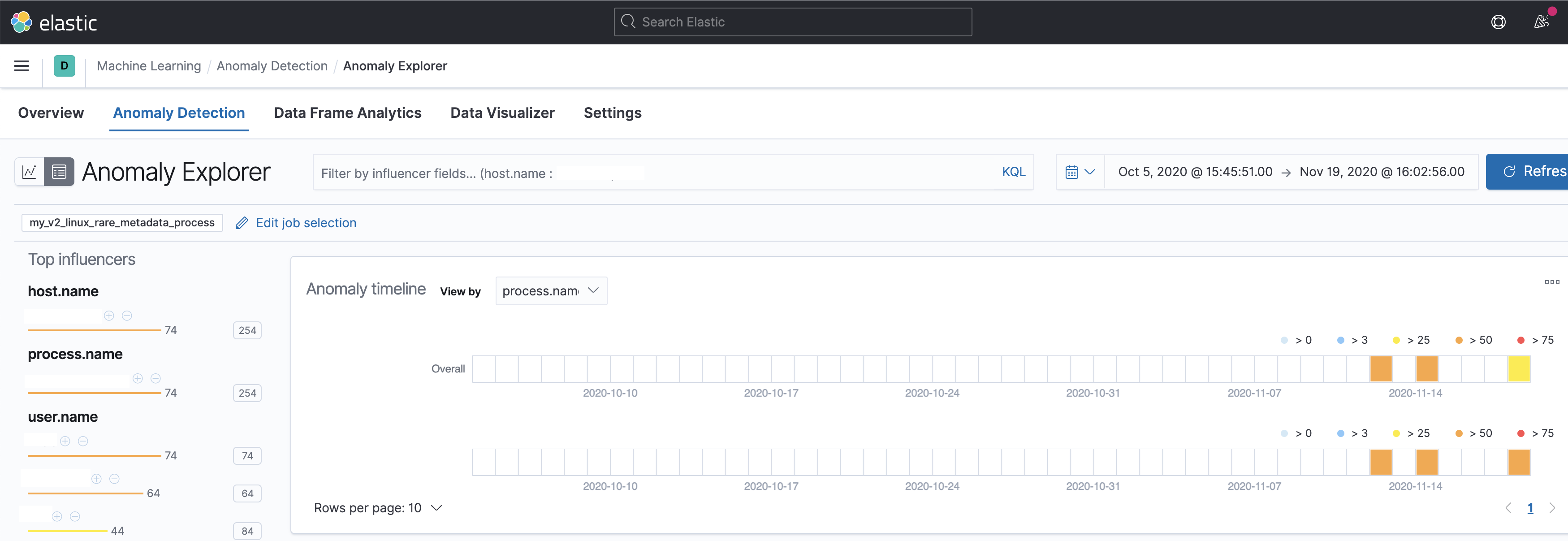
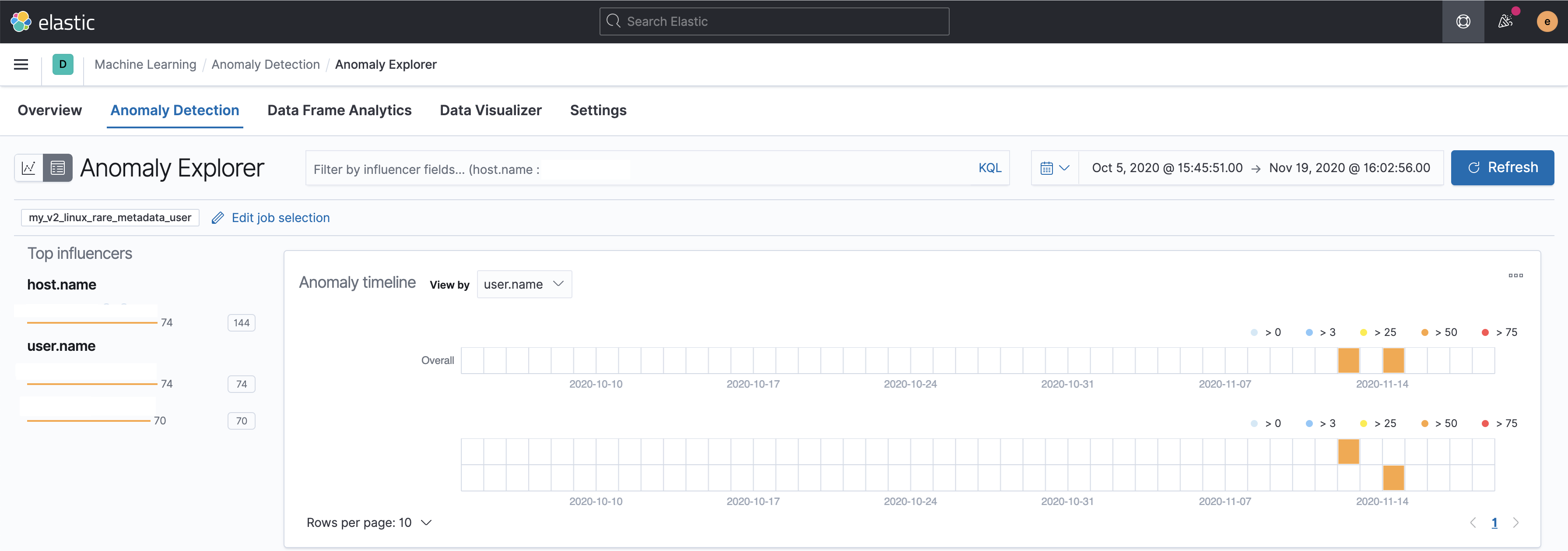
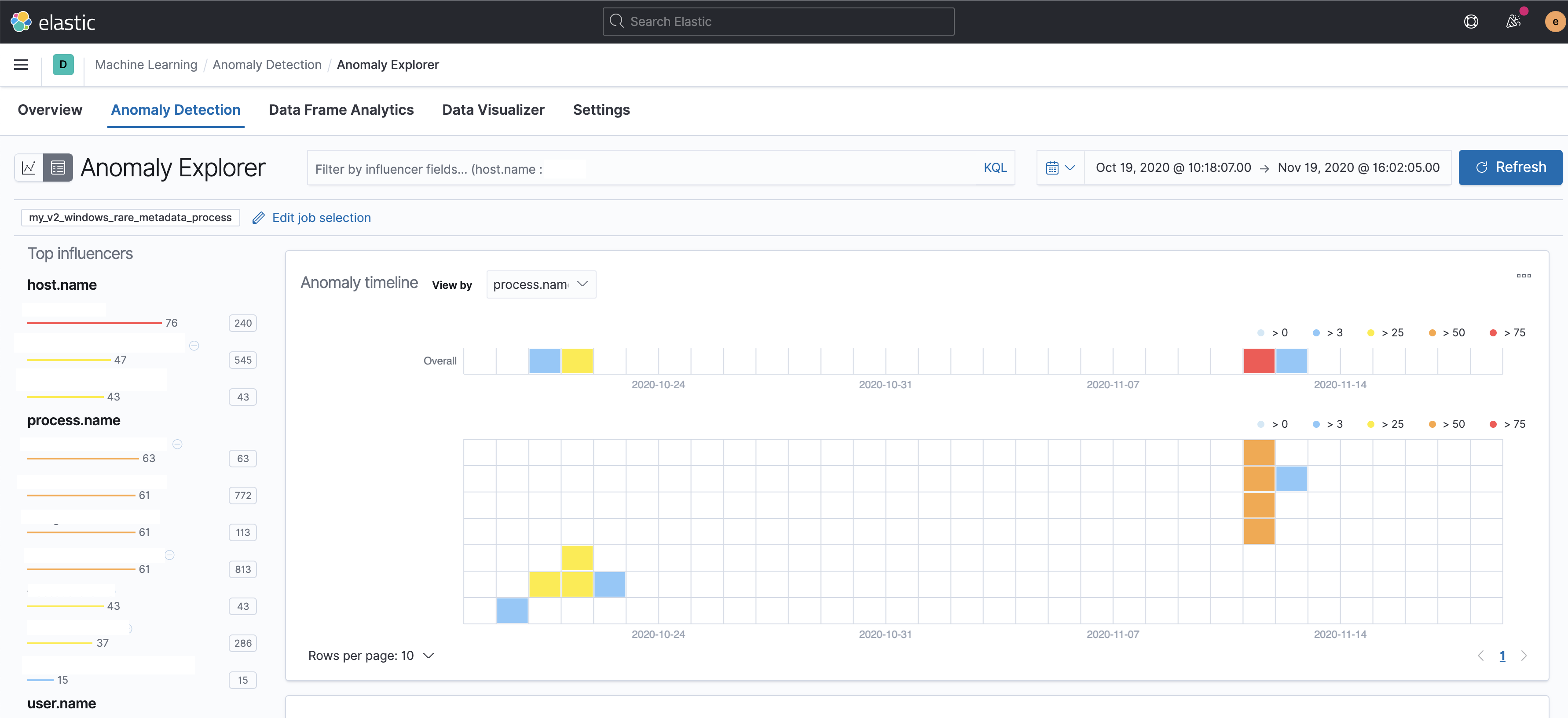
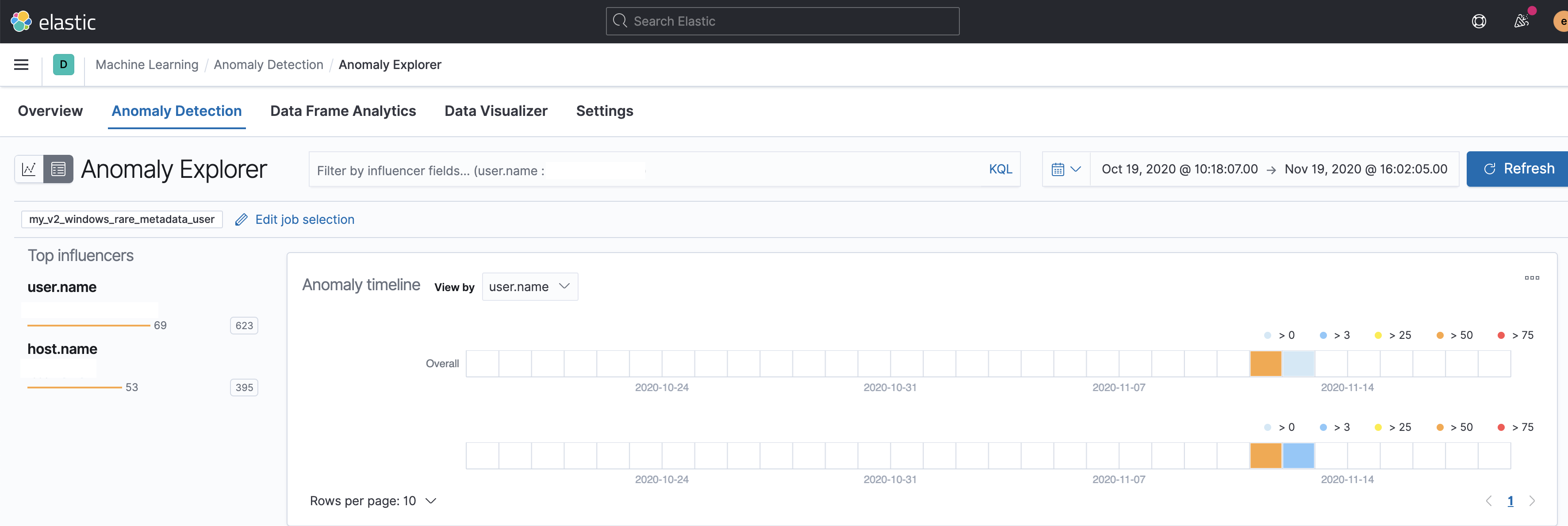
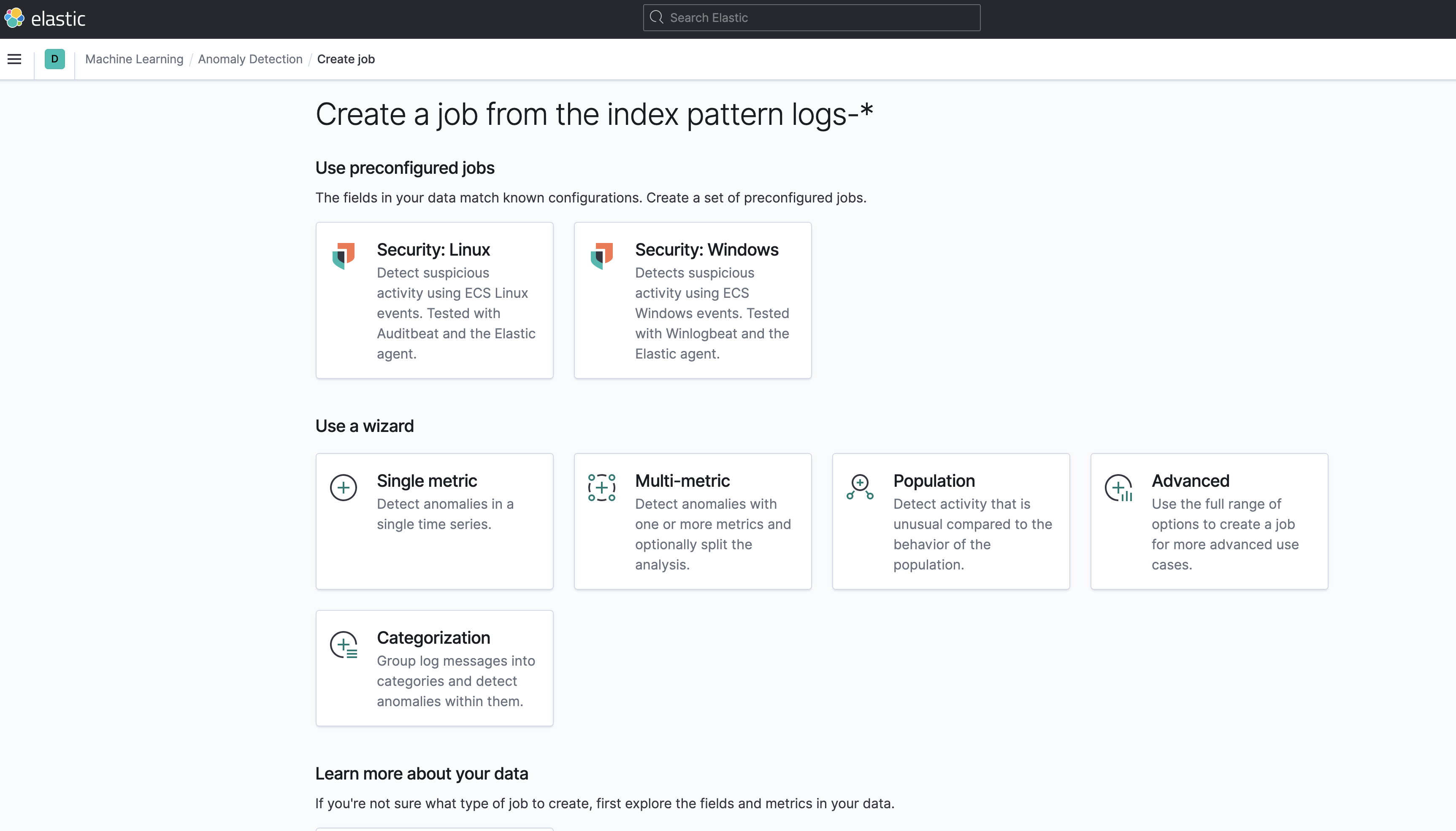
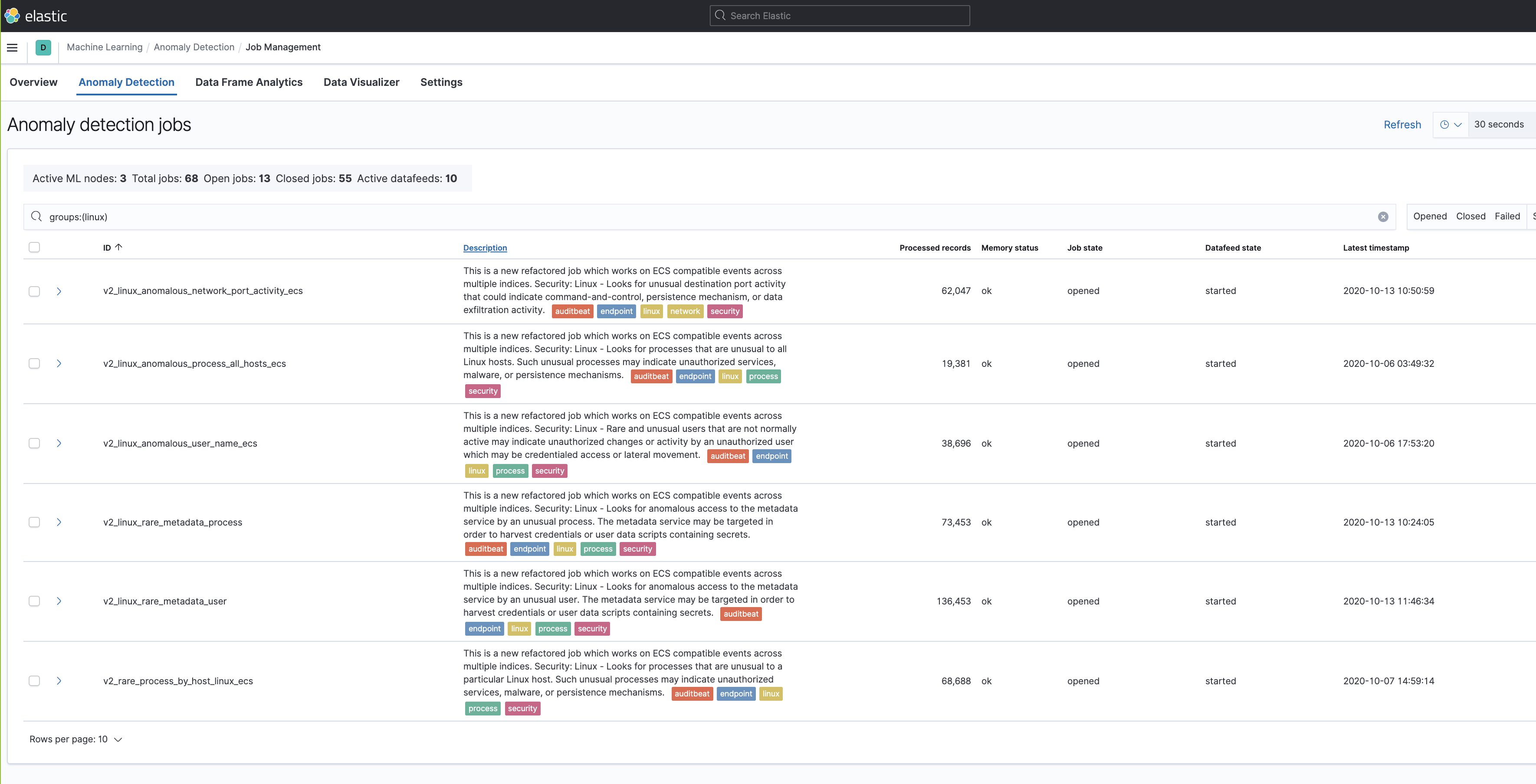
Summary
Adds the files for a 2 new modules -
security_linuxandsecurity_windows- for use within the Security app, containing the job and datafeed configuration files that support multi-index, multi-pipeline analyses across beats and agents that collect linux and windows data.Contains: