-
Notifications
You must be signed in to change notification settings - Fork 8.5k
Closed
Labels
Feature:Security/AuthenticationPlatform Security - AuthenticationPlatform Security - AuthenticationTeam:SecurityPlatform Security: Auth, Users, Roles, Spaces, Audit Logging, etc t//Platform Security: Auth, Users, Roles, Spaces, Audit Logging, etc t//enhancementNew value added to drive a business resultNew value added to drive a business result
Description
When during the SAML/OpenID Connect IdP initiated login or at the last step of SP initiated handshake Elasticsearch (e.g. Kibana session expired in the middle of SAML handshake #18117) rejects to authenticate user we just display raw error message without guiding user on what to do next.
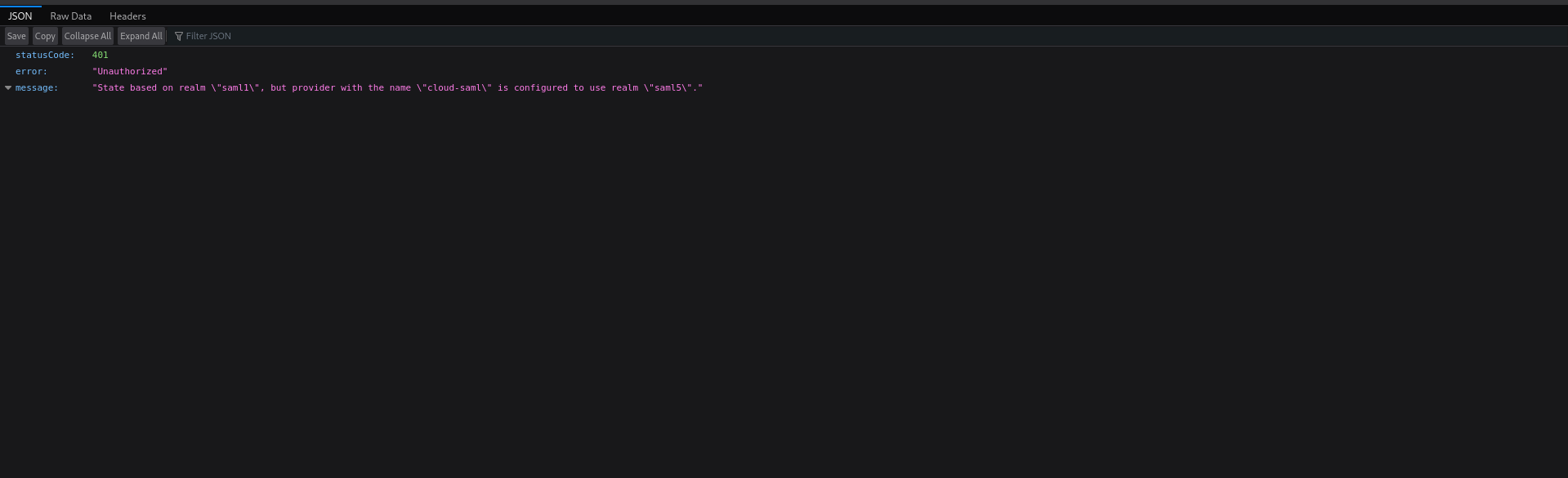
Here is example where user ends up with if SAMLResponse is rejected because of unknown realm:
We can detect most (all?) of these cases since they're triggered through dedicated endpoints (/api/security/saml/callback, /internal/security/saml/start, /api/security/oidc/callback and /api/security/oidc/initiate_login) and render something that is nicer and more actionable than that.
legrego
Metadata
Metadata
Assignees
Labels
Feature:Security/AuthenticationPlatform Security - AuthenticationPlatform Security - AuthenticationTeam:SecurityPlatform Security: Auth, Users, Roles, Spaces, Audit Logging, etc t//Platform Security: Auth, Users, Roles, Spaces, Audit Logging, etc t//enhancementNew value added to drive a business resultNew value added to drive a business result