-
Notifications
You must be signed in to change notification settings - Fork 3.3k
[Reference] freshness project: Profile (az account, az login)
#24633
New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
[Reference] freshness project: Profile (az account, az login)
#24633
Conversation
|
Reference |
|
@jiasli, do I understand correctly that autogen content can only handle one line per code block? These are separate lines in the PY. |
|
Link to #24332 |
|
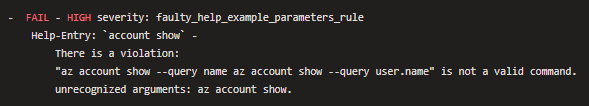
@dbradish-microsoft, this is because one line break is converted to space in a text: >
az account show --query name
az account show --query user.nameIf you want to make a line break, use text: >
az account show --query name
az account show --query user.nameAlso, you may use text: |
az account show --query name
az account show --query user.name |
| subscriptionId="$(az account list --query "[?contains(name, 'OneOfMySubscriptionNames')].id" --output tsv)" | ||
| az account set --subscription $subscriptionId | ||
| echo "The current subscription has been set to $subscriptionId" |
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
Similar to #24332 (comment)
These lines can simply be done with
az account set --subscription OneOfMySubscriptionNames
| - name: List all enabled subscriptions. | ||
| text: az account list | ||
| - name: Get the current default subscription. | ||
| text: az account list --query "[?isDefault]" |
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
This example has little real-world usage, as it can be replaced by az account show. Only one subscription can have isDefault==True.
| - name: Log in with a password containing a `-` as the first character. | ||
| text: az login --user [email protected] --password=-myPasswordThatStartsWithAdash | ||
| - name: Log in with a service principal using a client secret. | ||
| text: az login --service-principal --user http://azure-cli-2016-08-05-14-31-15 --password VerySecret --tenant contoso.onmicrosoft.com |
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
We now recommend using tenant ID, instead of domain name, as domain name requires extra resolution (#10418):
| def validate_tenant(cmd, namespace): | |
| """ | |
| Make sure tenant is a GUID. If domain name is provided, resolve to GUID. | |
| https://docs.microsoft.com/azure/active-directory/develop/v2-protocols-oidc#fetch-the-openid-connect-metadata-document | |
| """ | |
| from azure.cli.core.util import is_guid | |
| if namespace.tenant is not None and not is_guid(namespace.tenant): | |
| import requests | |
| active_directory_endpoint = cmd.cli_ctx.cloud.endpoints.active_directory | |
| url = '{}/{}/.well-known/openid-configuration'.format(active_directory_endpoint, namespace.tenant) | |
| response = requests.get(url, verify=not should_disable_connection_verify()) | |
| if response.status_code != 200: | |
| from knack.util import CLIError | |
| raise CLIError("Failed to resolve tenant '{}'.\n\nError detail: {}".format(namespace.tenant, response.text)) | |
| # Example issuer: https://sts.windows.net/72f988bf-86f1-41af-91ab-2d7cd011db47/ | |
| tenant_id = response.json()['issuer'].split("/")[3] | |
| logger.debug('Resolved tenant domain name %s to GUID %s', namespace.tenant, tenant_id) | |
| namespace.tenant = tenant_id |
| long-summary: If no subscription is specified, shows the current subscription. | ||
| long-summary: If no subscription is specified, information for the current subscription is returned. | ||
| examples: | ||
| - name: Get the current default subscription returning results in your default format. |
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
returning results in your default format
This applies to all commands, not only az account show.
| - name: Change the active subscription using a variable. | ||
| text: > | ||
| # Bash script | ||
| subscriptionId="$(az account list --query "[?contains(name, 'OneOfMySubscriptionNames')].id" --output tsv)" |
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
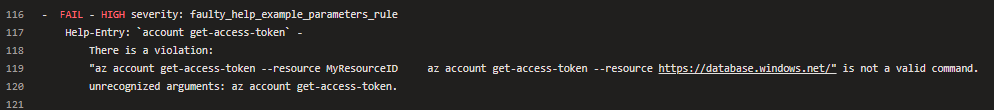
| text: > | ||
| az account get-access-token --resource MyResourceID |
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
| text: > | |
| az account get-access-token --resource MyResourceID | |
| text: az account get-access-token --resource https://management.azure.com/ |
https://management.azure.com/ is a more concrete example compared to MyResourceID.
| text: az account get-access-token --tenant MySubscriptionID | ||
| - name: Get an access token information to use with MS Graph API. | ||
| text: az account get-access-token --resource-type ms-graph | ||
| - name: Get an access token information for a particular resource. If you receive a `Failed to connect to MSI...` error, your resource may not exist. |
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
Failed to connect to MSI... is a Cloud Shell bug. It is not related to non-existing resource.
| - name: Get an access token information for a particular resource. If you receive a `Failed to connect to MSI...` error, your resource may not exist. | |
| - name: Get an access token information for a particular resource. |
| - name: Get an access token information for a particular resource. If you receive a `Failed to connect to MSI...` error, your resource may not exist. | ||
| text: > | ||
| az account get-access-token --resource MyResourceID | ||
| - name: Get only the access token for a particular resource returning results in plain text. This script is useful when you want to store the token in a variable. |
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
| - name: Get only the access token for a particular resource returning results in plain text. This script is useful when you want to store the token in a variable. | |
| - name: Get only the access token for a particular resource returning results in plain text. This command is useful when you want to store the token in a variable. |
| az account get-access-token --resource MyResourceID | ||
| - name: Get only the access token for a particular resource returning results in plain text. This script is useful when you want to store the token in a variable. | ||
| text: az account get-access-token --resource https://management.core.windows.net/ --query accessToken --output tsv | ||
| - name: Get an access token for a particular scope |
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
| - name: Get an access token for a particular scope | |
| - name: Get an access token information for a particular scope |
We may make it consistent with other examples.
| text: az login --service-principal --user http://azure-cli-2016-08-05-14-31-15 --password VerySecret --tenant contoso.onmicrosoft.com | ||
| - name: Log in with a service principal using a client certificate. | ||
| text: aaz login --service-principal --user http://azure-cli-2016-08-05-14-31-15 --password ~/MyCertfile.pem --tenant contoso.onmicrosoft.com | ||
| - name: Log in using a VM's system assigned identity. |
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
| - name: Log in using a VM's system assigned identity. | |
| - name: Log in using default managed identity. |
Not only VM has managed identity.
Also, if no system-assigned identity is configured, but a user assigned identity is, this command uses the user-assigned identity as the default one.
If both system-assigned identity and user-assigned identity are configured, system-assigned identity is chosen as the default.
| Get specific information about a subscription using `--query`. | ||
| To see available query options, first run `az account show --output json`. | ||
| For in-depth `--query` examples see [How to query Azure CLI command output using a JMESPath query](https://learn.microsoft.com/cli/azure/query-azure-cli). |
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
As discussed in #24332 (comment), I am hesitating on whether we want to add examples for generic argument --query.
| - name: Log in with a service principal using a client secret. | ||
| text: az login --service-principal --user http://azure-cli-2016-08-05-14-31-15 --password VerySecret --tenant contoso.onmicrosoft.com | ||
| - name: Log in with a service principal using a client certificate. | ||
| text: aaz login --service-principal --user http://azure-cli-2016-08-05-14-31-15 --password ~/MyCertfile.pem --tenant contoso.onmicrosoft.com |
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
| text: aaz login --service-principal --user http://azure-cli-2016-08-05-14-31-15 --password ~/MyCertfile.pem --tenant contoso.onmicrosoft.com | |
| text: az login --service-principal --user http://azure-cli-2016-08-05-14-31-15 --password ~/MyCertfile.pem --tenant contoso.onmicrosoft.com |
| text: aaz login --service-principal --user http://azure-cli-2016-08-05-14-31-15 --password ~/MyCertfile.pem --tenant contoso.onmicrosoft.com | ||
| - name: Log in using a VM's system assigned identity. | ||
| text: az login --identity | ||
| - name: Log in using a VM's user assigned identity. Client or object ids of the service identity also work. |
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
| - name: Log in using a VM's user assigned identity. Client or object ids of the service identity also work. | |
| - name: Log in using a VM's user-assigned identity. Client ID or object ID of the user-assigned identity also works. |
There should be a hyphen in user-assigned: https://learn.microsoft.com/en-us/azure/active-directory/managed-identities-azure-resources/overview
| - name: Log in using a VM's system assigned identity. | ||
| text: az login --identity | ||
| - name: Log in using a VM's user assigned identity. Client or object ids of the service identity also work. | ||
| text: az login --identity --user /subscriptions/MySubscriptionID/resourcegroups/MyResourceGroup/providers/Microsoft.ManagedIdentity/userAssignedIdentities/myID |
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
| text: az login --identity --user /subscriptions/MySubscriptionID/resourcegroups/MyResourceGroup/providers/Microsoft.ManagedIdentity/userAssignedIdentities/myID | |
| text: az login --identity --username /subscriptions/MySubscriptionID/resourcegroups/MyResourceGroup/providers/Microsoft.ManagedIdentity/userAssignedIdentities/myID |
| text: > | ||
| az account show --query user.name |
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
| text: > | |
| az account show --query user.name | |
| text: az account show --query user.name |
| # Bash script | ||
| subscriptionId="$(az account show --query id --output tsv)" | ||
| echo "The current subscription ID is $subscriptionId" |
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
Extra line break is needed as L84 uses >, not |.
We can test the rendered help message by running az account show --help.
| short-summary: Get a token for utilities to access Azure. | ||
| long-summary: > | ||
| The token will be valid for at least 5 minutes with the maximum at 60 minutes. | ||
| The token will be valid for at least 5 minutes with a maximum of 60 minutes. |
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
This will no longer be the case once CAE is enabled. We'd better not mention such implementation detail. The user should always check the expiresOn property of the returned JSON.
Also see #19700
|
I am giving the methodology for freshening azCLI autogen reference content, and consequently this PR, a necessary ending in order to make way for new beginnings. |
This PR is part of the reference refresh project. This PR focuses on
src/azure-cli/azure/cli/command_modules/profile/_help.pyand any related file containing summaries or examples for these same command groups.The updates in this PR are intended to freshen the following reference areas:
Note: The testing of all examples is out of scope for this project and is part of the Content Quality Automation crew project.
This is work item https://dev.azure.com/mseng/TechnicalContent/_workitems/edit/1998772.
This checklist is used to make sure that common guidelines for a pull request are followed.
The PR title and description has followed the guideline in Submitting Pull Requests.
I adhere to the Command Guidelines.
I adhere to the Error Handling Guidelines.