-
Notifications
You must be signed in to change notification settings - Fork 48
New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
Incorrectly parse cookies containing comma in value. #28
Comments
|
For people looking for a workaround, I do have one. By adding manual value parsing instead of relying on headers = [] # array of set-cookie header
uri = 'https://example.com'
jar = HTTP::CookieJar.new
kv_matcher = /\A([^\s=]*?)\s*=\s*([^\n;]*?)\s*(?:;|\z)/i
headers.each do |header|
matched_data = kv_matcher.match(header)
# next unless matched_data
jar.parse(header, uri) do |cookie|
cookie_name = matched_data[1]
cookie_value = matched_data[2]
cookie.name = cookie_name unless (cookie.name == cookie_name)
cookie.value = cookie_value unless (cookie.value == cookie_value)
cookie
end
endIt works for my use case, but I can't guarantee it will work according to the standard. |
|
Digging further, trying to send a pull request. I feel the need to disclose that the header was from Linkedin. Here why the task is impossible:
The only solution is to drop support for such gem, it is not how HTTP headers are supposed to work in the first place. I truly hope some enterprises can pick this up. |
|
No response so far. |
It is possible for a cookie to contains a comma in its value.
This is the real header I found in the wild:
Chrome parses it as
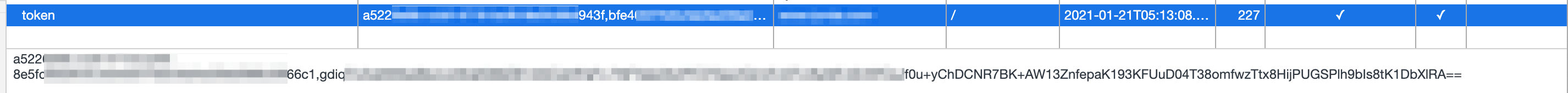
name: token
value: 2e732538-f38e-ae67-8217-5330686854ee,35cfb541def868b6778c0dc45e368322,hWiqTu7qtWt6wBbcUzWqK018Zb1iA5CeHPafl+7nFyAlE3XzPFCFsav2QrmFcSTLlnYNFvlS/7PCsJf9u+ychIZQFY4JGZb4dSoEIgaLtNKWEcD+/hHrAnUEaAtOg7ChfTbN42PS3wPhxOtAI5RcLw==
However, this gem parses it as
name: 35cfb541def868b6778c0dc45e368322,hWiqTu7qtWt6wBbcUzWqK018Zb1iA5CeHPafl+7nFyAlE3XzPFCFsav2QrmFcSTLlnYNFvlS/7PCsJf9u+ychIZQFY4JGZb4dSoEIgaLtNKWEcD+/hHrAnUEaAtOg7ChfTbN42PS3wPhxOtAI5RcLw
value: =
Which cause errors.
The text was updated successfully, but these errors were encountered: